Weaponized Installer Lab
🛠️ Overview
Weaponized Installer Lab is an offensive security simulation project designed to replicate real-world payload delivery techniques. This labs walks through building a trojanized installer that delivers encrypted Sliver shellcode, simulating a user falling victim to a social engineering attack. The project aims to highlight practical adversary workflows from command and control (C2) setup to payload encryption, obfuscation, and final execution on a target machine.
🔗 Github Repository
View the full project on Github
🔍 Key Objectives
- Simulate a modern red team operation in a controlled environment
- Demonstrate payload generation, encryption , and delivery methods
- Serve as a portfolio example of realistic adversary simulation
🔐 Lab Highlights
- Sliver C2 setup with HTTP listener
- Shellcode generation and RC4 encryption for stealth
- Nim Wrapper compiled with a legitimate installer
- Fake landing page simulation for user interaction
- Reverse shell established post-installation
🧰 Tools & Technologies

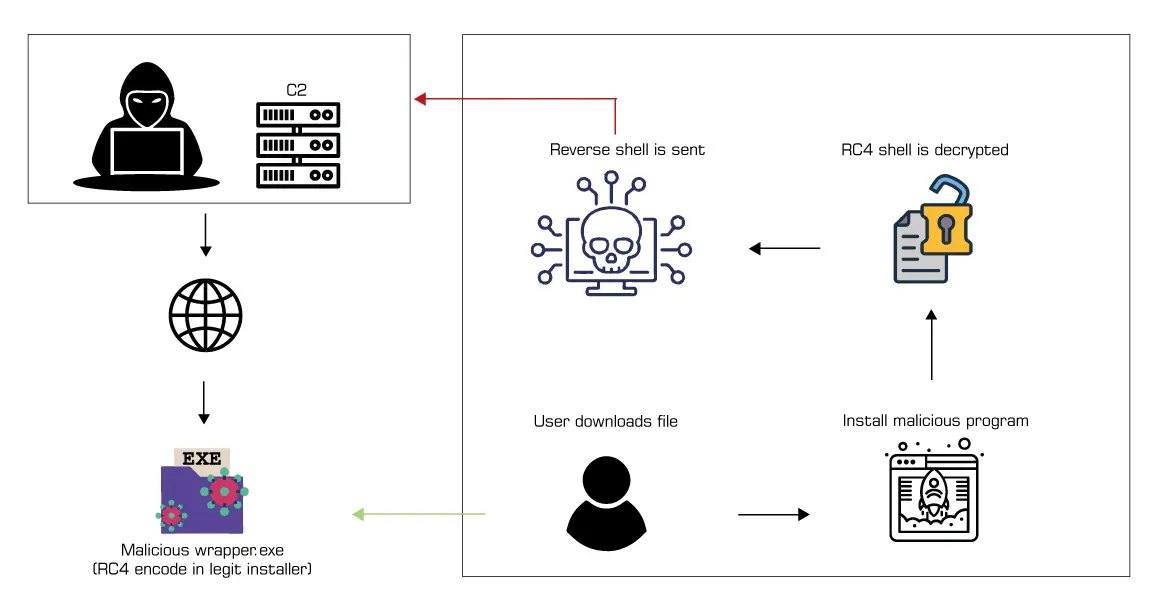
🔄 Workflow Summary
- Generate Sliver shellcode (‘.bin)
- Encrypt payload using RC4
- Wrap payload with legitimate installer using Nim
- Host on a fake landing page
- User installs the trojanized executable
- Callback to Sliver listener for post-exploitation access
⚠️ Disclaimer
This lab was created for educational and red teaming purposes only. All actions were performed in isolated lab environments under controlled conditions.